A synopsis of this post:
- Azure resource logs explained
- Explaining the Azure diagnostics mode (current / deprecating mode)
- Explaining the modernized Resource-specific mode
- The list of current Azure resources that support resource-specific mode
- How do we configure and test the new modernized resource-specific mode?
1. Azure resource logs explained
Azure resource logs are platform logs that provide insight into operations that were performed within an Azure resource. The content of resource logs varies according to the Azure service and resource type. Resource logging is not enabled and collected by default. Diagnostic logging needs to be manually enabled. The diagnostic settings need to be enabled on the specific Azure resources to enable each Azure resource to send its resource logs to respective destinations.
The current default destination for sending Azure resource logs is to the Log Analytics workspace AzureDiagnostics table. A new method will be to send Azure resource logs to multiple resource-specific tables for each category of the resource.
2. Explaining the Azure diagnostics mode (current / deprecating mode)
In this current mode, all data from any diagnostic settings is collected in the central AzureDiagnostics table. This legacy method is used today by most Azure services. Because multiple resource types send data to the same table, its schema is the superset of the schemas for all of the different data types being collected.
The AzureDiagnostics Table
The AzureDiagnostics table is a central storage table in the Log Analytics Workspace which stores resource logs for multiple Azure services that have the Azure Diagnostics enabled. Resource logs describe the internal operations of Azure resources.
Sending data to the legacy Log Analytics Workspace AzureDiagnostics table
Sending resource logs to a Log Analytics workspace is the current method of enabling the features of Azure Monitor Logs on a resource, where you can:
- Correlate resource log data with other monitoring data collected by Azure Monitor.
- Consolidate log entries from multiple Azure resources, subscriptions, and tenants into one location for analysis together.
- Use log queries to perform complex analysis and gain deep insights on log data.
- Use log alerts with complex alerting logic.
Enable diagnostic settings to send resource logs to a Log Analytics workspace. This data is stored in tables as described in Structure of Azure Monitor Logs. The tables used by resource logs depend on what type of collection the resource is using:
- Azure diagnostics: All data is written to the single AzureDiagnostics table (current / legacy methodology)
- Resource-specific: Data is written to multiple individual tables for each category of the resource (new methodology)
3. Explaining the modernized Resource-specific mode
In this new modernized mode, multiple individual tables are provisioned in the selected workspace for each category selected in the diagnostic setting. Microsoft recommends this method going forward because:
- Simplified means to work with the data in log queries.
- Provides improved discoverability of schemas and their structure.
- Improves performance across ingestion latency and query times.
- Provides the ability to grant Azure role-based access control rights on a specific table.
- All Azure services will eventually migrate to the resource-specific mode!
Certain Azure services may be configured to use either the resource-specific mode to store data in multiple tables specific to that service, or the legacy Azure diagnostics mode. When configured in resource-specific mode, the resources cannot send logs to the AzureDiagnostics table.
4. The list of current Azure resources that support resource-specific mode
The Resource Types list below shows the current Azure services that are able to send their logs to resource-specific tables. This list will be incrementally updated in the future as more Azure services / resources are modernized / enabled with the resource-specific logging mode, so keep monitoring this list.
The current list of resource-specific mode enabled Azure resources at the time of writing this blog are:
- API Management Services
- Azure Cosmos DB
- Data factories (V2)
- IoT Hub
- Recovery Services vaults(Backup)
Keep monitoring the Microsoft link below for updates to the Azure services list:
This post discusses the following points:
5. How do we configure and test the new modernized resource-specific mode?
To test the resource-specific mode in this post, I am provisioning a random Recovery Services vault in a sandbox.
Step 1 – Go to Azure Portal > Recovery Services Vault > Create.
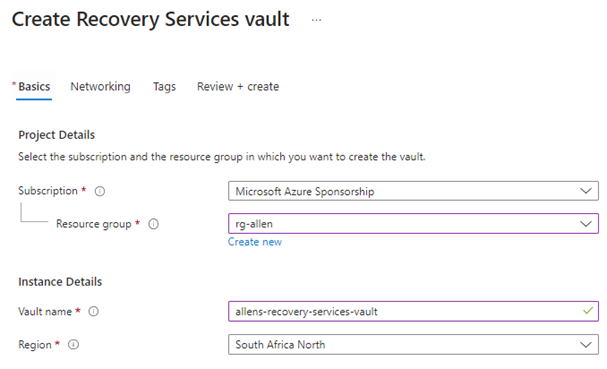
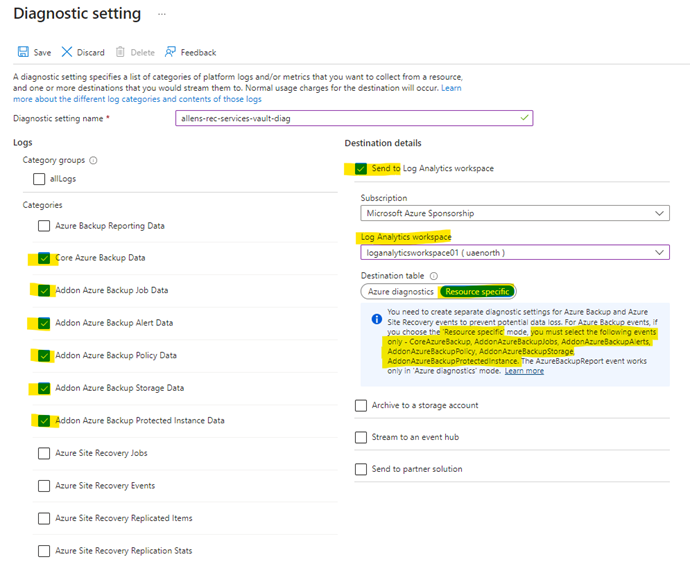
Step 2 – provision Diagnostic Settings on the RSV.
RSV > select Diagnostic Settings. Select + Add Diagnostic Setting.
Provide a bespoke unambiguous name to the diagnostics settings.
Select the Send to Log Analytics Workspace check box > select a destination Log Analytics workspace.
Select the Resource specific in the toggle, and select the following six events required for RSV:
CoreAzureBackup,AddonAzureBackupJobs, AddonAzureBackupAlerts, AddonAzureBackupPolicy, AddonAzureBackupStorage, AddonAzureBackupProtectedInstance.
Select Save.
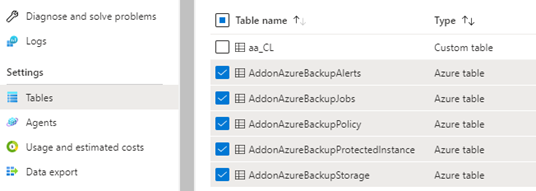
Step 3 – After the Diagnostic Settings has been enabled on the RSV, go to the destination Log Analytics Workspace > Tables.
After data begins flowing into the Log Analytics workspace (almost immediately), dedicated tables for each of these events are created in your workspace. You can query any of these tables directly. You can also perform joins or unions between these tables if necessary.
AddonAzureBackupAlerts
AddonAzureBackupJobs
AddonAzureBackupPolicy
AddonAzureBackupProtectedInstance
AddonAzureBackupStorage
CoreAzureBackup
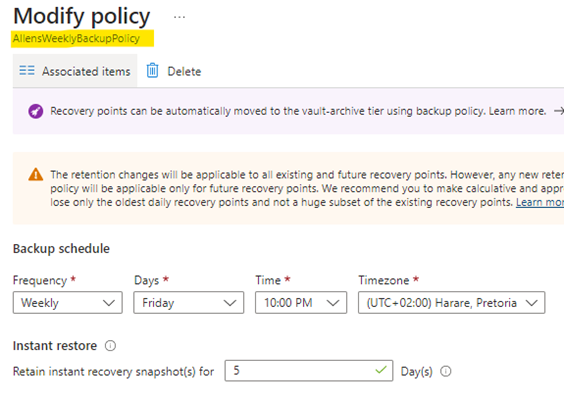
Here I create an Azure Recovery Services Vault Backup Policy in an effort to generate a database entry in the AddonAzureBackupPolicy table. The custom RSV Backup Policy is called “AllensWeeklyBackupPolicy” (which i will use below in my KQL query)
In the Azure Portal > Log Analytics Workspace > Logs > I ran a query on the AddonAzureBackupPolicy database to confirm that a database entry was created in the resource-specific table.
AddonAzureBackupPolicy|
order by TimeGenerated desc | where PolicyName contains "AllensWeeklyBackupPolicy"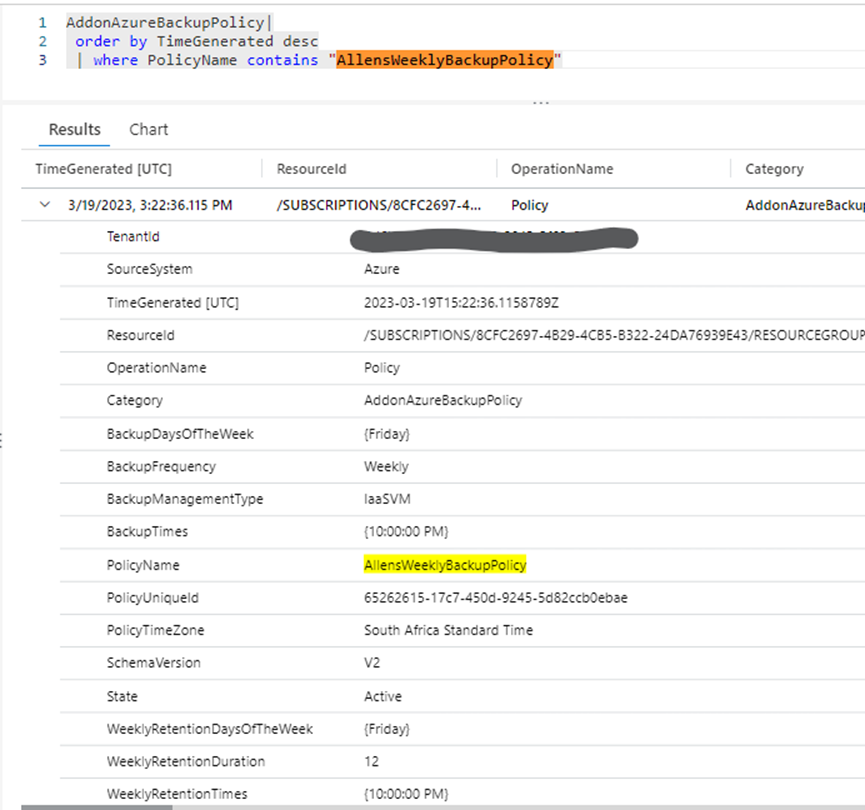
The end-user verification is successfull since we can see that the resource-specific AddonAzureBackupPolicy database has been populated with the new Azure Backup Policy log showing the AllensWeeklyBackupPolicy provisioning.
I was wondering if you ever considered changing the layout of your website? Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people could connect with it better. Youve got an awful lot of text for only having 1 or 2 images. Maybe you could space it out better?
I view something truly special in this site.
May I request that you elaborate on that? Your posts have been extremely helpful to me. Thank you!
Excellent post. I am going through a few of these issues as well..
I’m impressed, I have to admit. Rarely do I encounter a blog that’s equally educative and engaging, and without a doubt, you have hit the nail on the head. The problem is something too few folks are speaking intelligently about. Now i’m very happy I stumbled across this in my hunt for something relating to this.
A great post without any doubt.
Everyone loves what you guys are usually up too. This sort of clever work and reporting! Keep up the awesome works guys I’ve included you guys to my own blogroll.
An outstanding share! I have just forwarded this onto a co-worker who had been doing a little research on this. And he in fact ordered me breakfast simply because I found it for him… lol. So let me reword this…. Thank YOU for the meal!! But yeah, thanx for spending time to discuss this matter here on your web page.
This is a topic which is near to my heart… Cheers! Exactly where are your contact details though?
Thanks, I’ve been searching for facts about this subject for ages and yours is the best I’ve discovered so far.
Good post. I will be dealing with some of these issues as well..
We are a group of volunteers and opening a new scheme in our community. Your website offered us with valuable information to work on. You have done a formidable job and our entire community will be grateful to you.
Nice post. I learn something totally new and challenging on sites I stumbleupon every day. It will always be exciting to read content from other authors and practice something from their websites.
I love looking through an article that will make men and women think. Also, thank you for allowing me to comment.
You have made some decent points there. I checked on the net for more information about the issue and found most people will go along with your views on this website.
Excellent goods from you, man. I have understand your stuff previous to and you are just too magnificent. I really like what you have acquired here, really like what you’re stating and the way in which you say it. You make it entertaining and you still care for to keep it sensible. I can’t wait to read far more from you. This is really a terrific web site.