The aim of my blog is to quickly and easily deploy a virtual network with encryption using a 3-step modular powershell approach.
Virtual network encryption allows you to seamlessly encrypt and decrypt internal network traffic between Azure Virtual Machines (and Virtual Machines Scale Sets) with minimal impact to performance.
The aim of Azure virtual network encryption is to protect data traversing between Azure virtual machines residing on your Azure virtual network (regionally and globally peered ) as well as hybrid architectures, between Azure virtual machines and your on-premises networks.
Azure Virtual Network encryption is currently in preview. This preview version is provided without a service level agreement, and it’s not recommended for production workloads.
Dependencies – 8 things to know before enabling virtual network encryption
Enabling encryption on your Azure virtual network
Verify the encryption on your virtual network
Dependencies:
8 things to know before enabling virtual network encryption:
#1 Region:
Verify that your virtual network is eligible for virtual network encryption by checking availability
#2 Virtual Machine SKUs:
Azure Virtual Network encryption is dependent on supported virtual machine SKUs in the virtual network for traffic to be encrypted. Traffic between unsupported virtual machine SKUs will be dropped on the virtual network,
Verify the list of currently supported SKU’s

Traffic to unsupported Virtual Machines will remain unencrypted,
#3 Accelerated Networking:
Must be enabled on the network interfaces of the virtual machines,
#4 Private IP:
Encryption is only applied to private ip traffic between virtual machines in a virtual network. This does not apply to public ip interfaces.
#5 Internal load balancers:
When using an Internal load balancer, all the virtual machines behind the load balancer must be compliant according to the virtual machine SKU’s,
#6 PaaS Services:
Where a PaaS is involved, the virtual machine SKU dictates if virtual network encryption is supported,
#7 Global Peering:
Is supported in regions where virtual network encryption is supported,
#8 Post encryption enablement:
The start/stop of existing virtual machines may be required after enabling encryption in a virtual network
Enabling encryption on your Azure virtual network
There are 2 ways to easily enable virtual network encryption,
Azure Portal
Go to overview > properties > encryption > click on the Disabled link to open the next window >
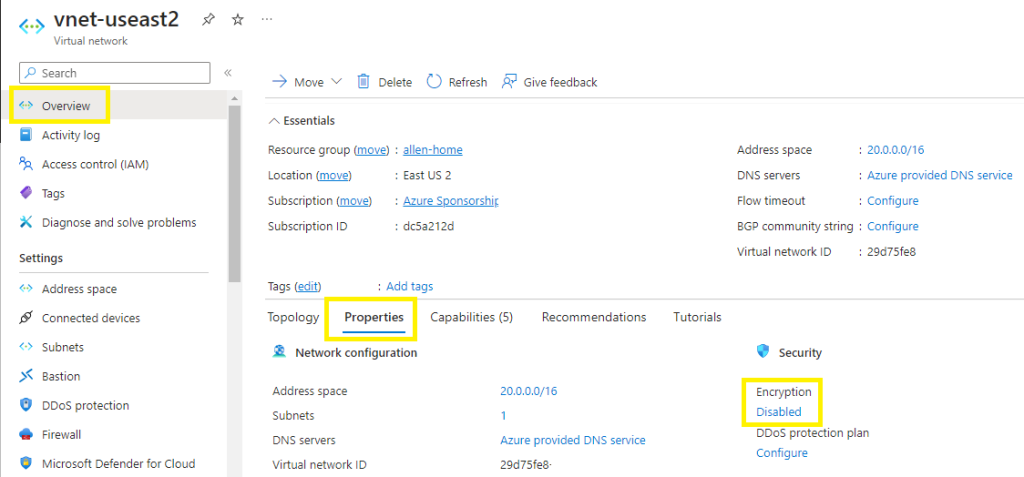
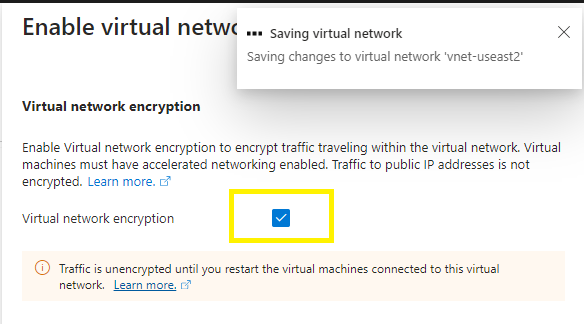
Select the checkbox and Save
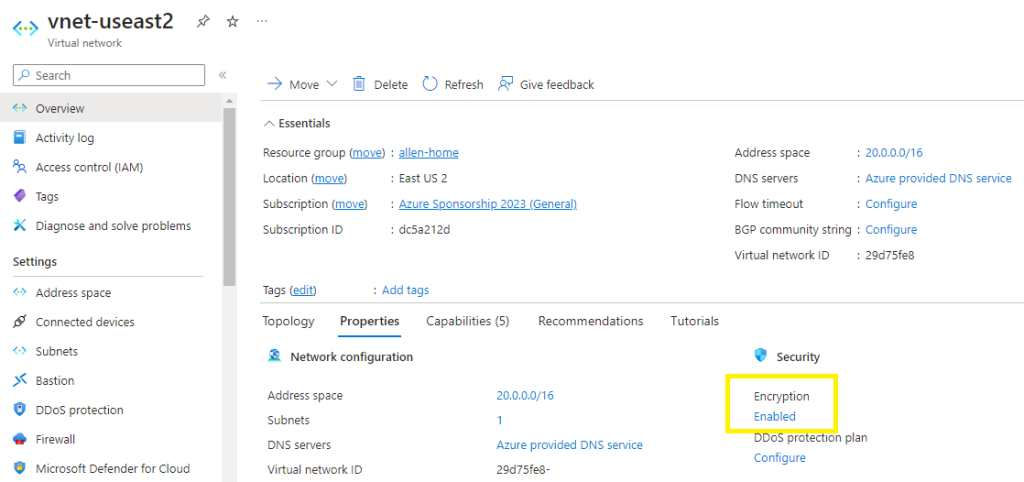
Verification
Go to back to your overview > properties > encryption > your encryption will now be enabled,
Powershell
Step 1 – New Resource Group
Create your new resource group container for your virtual network resources, with tagging:
#create a resource group for the primary vnet infrastructure and its resources#
$rgName = "allen-sandbox-vnet"
$location = "eastus2"
New-AzResourceGroup `
-Name $rgName `
-Location $location `
-Tag @{CustomerName="Customer01"; AutoShutdownSchedule="None"; Environment="sandbox";}Step 2 – Create your subnet
##Create your subnet/s
$subnet1name = "Internal-subnet01"
$subnet1cidr = "10.0.1.0/27"
$subnet = @{
Name = $subnet1name
AddressPrefix = $subnet1cidr
}
$subnet
$subnetConfig = New-AzVirtualNetworkSubnetConfig @subnet Step 3 – Create your virtual network
Create your virtual network and include your subnet created previously. The script below provides the option to create tags for your virtual network.
$vnetname = "vnet-eastus2"
$vnetcidr = "10.0.0.0/16"
# Add tags to the primary virtual network
$tags = @{"CustomerName"="Customer01"; "AutoShutdownSchedule"="None";"Environment"="sandbox" }
$tags
$net = @{
Name = $vnetname
ResourceGroupName = $rgName
Location = $location
AddressPrefix = $vnetcidr
Subnet = $subnetConfig
EnableEncryption = 'true'
EncryptionEnforcementPolicy = 'AllowUnencrypted'
Tag = $tags
}
New-AzVirtualNetwork @net(Optional) Step 4 – Apply the no-delete lock to the production primary infra virtual network
New-AzResourceLock `
-LockLevel CanNotDelete `
-LockNotes "No delete lock applied during deployment" `
-LockName "no-delete-customer-lock" `
-ResourceName $vnetname `
-ResourceGroupName $rgname `
-ResourceType "Microsoft.Network/virtualNetworks" `
-forceVerify the encryption on your virtual network
## Place the virtual network configuration into a variable. ##
$net = @{
Name = $vnetname
ResourceGroupName = $rgName
}
$vnet = Get-AzVirtualNetwork @net
$vnet.Encryption
Virtual Network Flow Logs
Virtual Network Flow Logs to confirm flow encryption between virtual machines here.
–I hope this blog helped to easily enable encryption on your virtual network–

Sustain the excellent work and producing in the group!
The articles you write help me a lot and I like the topic
I enjoyed reading your piece and it provided me with a lot of value.
Sustain the excellent work and producing in the group!
May I have information on the topic of your article?