Synopsis of this post:
- What is SQL Insights
- Take note of the current limitations of SQL Insights (preview)
- Pricing
- Regional Availability
- Components required for SQL Insights provisioning
- SQL backend
- Log Analtyics Workspace
- Ubuntu virtual machine
- Azure Key Vault
- Azure SQL telegraf user*
- SQL Monitor profile
- Provisioning of SQL Insights
- Step 1 – Provision SQL database
- System Assigned Managed Identity
- Step 2 – Configure Azure SQL Database Firewall settings
- Step 3 – Provision a destination Log Analytics workspace
- Step 4 – Provision the Data Collector Ubuntu Azure Virtual Machine
- The Azure Ubuntu virtual machine requirements
- System Assigned Managed Identity
- Enable Service Endpoint “Microsoft.Sql”
- Step 5 – Provision an Azure Key Vault
- Access Policy
- Generate Secret
- Step 6 – Create the SQL monitoring telegraf user account
- Step 7.1 – Create a SQL monitoring profile
- Step 7.2 – Adding a monitoring machine
- Step 8 – Verify Collection logs
- Step 1 – Provision SQL database
My post presumes that you already have a backend Azure SQL database in place and that you now want to enable SQL Insights. I have written this post using Azure SQL database but Azure SQL Insights can be used on Azure SQL Managed Instance and SQL Server ( Azure SQL family).
My post describes how to enable SQL Insights (preview) to monitor your SQL deployments. SQL Monitoring is performed via an Azure Ubuntu virtual machine that makes a connection to your SQL deployments to gather monitoring data. SQL Monitoring Profiles create Data Collection Rules (DCRs) that control what datasets are collected and the frequency of collection on each dedicated vm.
1. What is SQL Insights?
SQL Insights (preview) is a comprehensive solution for monitoring any product in the Azure SQL family. SQL Insights uses dynamic management views to expose the data that you need to monitor SQL health, diagnose problems, and tune performance.
SQL Insights performs all monitoring remotely. Monitoring agents are installed on dedicated (Ubuntu) virtual machines which connect to your SQL resources via DCR deployment and remotely gather data. The gathered data is stored in destination Log Analytics Workspace/s for easy aggregation, filtering, and trend analysis
The diagram below details the flow of information from the database engine and Azure resource logs, and how they can be parsed.
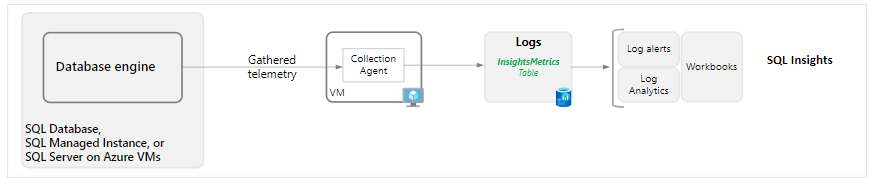
2. Current Limitations of SQL Insights (preview):
- Non-Azure instances: SQL Server running on virtual machines outside Azure is not supported.
- Azure SQL Database elastic pools: Metrics can’t be gathered for elastic pools or for databases within elastic pools.
- Azure SQL Database low service tiers: Metrics can’t be gathered for databases on Basic, S0, S1, and S2 service tiers.
- Azure SQL Database serverless tier: Metrics can be gathered for databases through the serverless compute tier. However, the process of gathering metrics will reset the auto-pause delay timer, preventing the database from entering an auto-paused state.
- Secondary replicas: Metrics can be gathered for only a single secondary replica per database. If a database has more than one secondary replica, only one can be monitored.
- Authentication with Azure Active Directory: The only supported method of authentication for monitoring is SQL authentication. For SQL Server on Azure Virtual Machines, authentication through Active Directory on a custom domain controller is not supported.
3. Pricing
There is no cost for the SQL Insights (preview) service. All costs are incurred by the virtual machines that gather the data, and the Log Analytics workspaces that store the ingested data, as well as any alert rules configured on the data.
4. Regional availability
SQL Insights (preview) is available in all Azure regions where Azure Monitor is available, with the exception of Azure Government and national clouds.
5. Components required for SQL Insights provisioning
- SQL backend
- Log Analtyics Workspace
- Ubuntu virtual machine
- Azure Key Vault
- Azure SQL telegraf user*
- SQL Monitor profile
6 -Provisioning of SQL Insights
Step 1 – Provision SQL database
You may be testing the SQL Insights on an existing SQL database which means that you can skip to step 2.
If you are testing the SQL Insights and want to deploy a new test Azure SQL database in a sandbox, then follow this url and deploy, https://learn.microsoft.com/en-us/azure/azure-sql/database/single-database-create-quickstart?view=azuresql&tabs=azure-portal
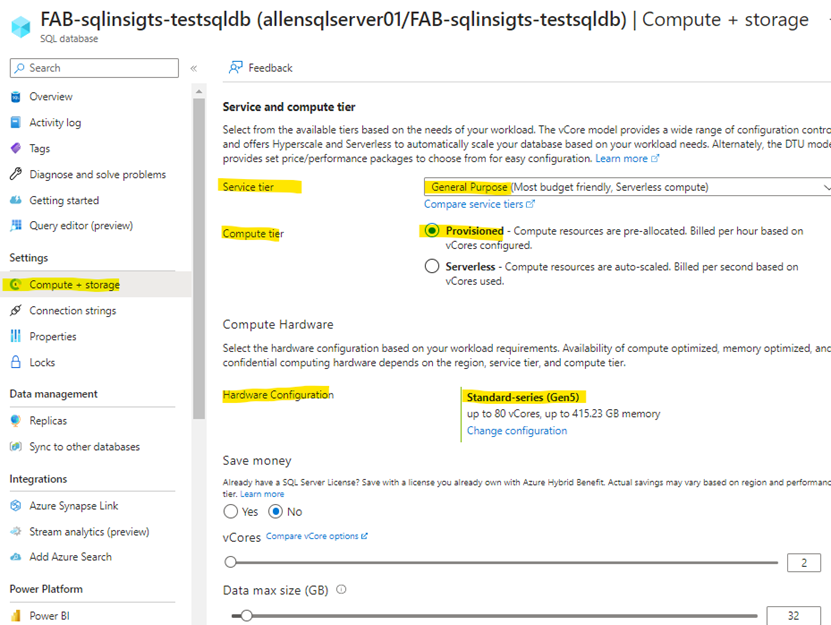
I followed these parameters while deploying a single database,
Using SQL authentication (AD authentication has not yet been released),
Dont deploy a SQL elastic pool,
Deploy only a Provisioned database (serverless is not yet fully functional),
Deploy General Purpose so that the db is not low service tier,
Use a public endpoint and add your devices IP,
Allow Azure services to access the server,
I chose Connection Policy = Redirect,
In the Additional settings tab, in the Data source section, I chose Use existing data, and selected the Sample database.
When you provision your new SQL Server, use the Admin name = telegraf and pick a password you will use again later in your Key Vault secret.
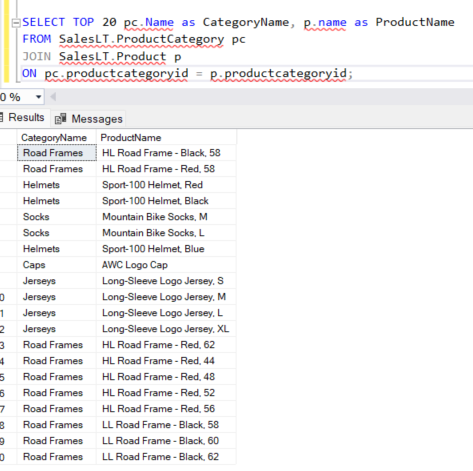
Once deployed > go to your SQL database > Query editor (preview) > login with telegraf > and run the following script to make sure your table is working:
SELECT TOP 20 pc.Name as CategoryName, p.name as ProductName
FROM SalesLT.ProductCategory pc
JOIN SalesLT.Product p
ON pc.productcategoryid = p.productcategoryid;
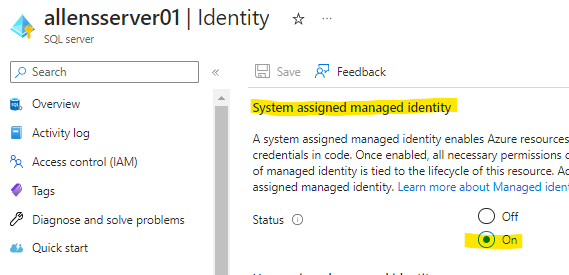
System Assigned Managed Identity
Once the SQL server has been deployed, go to the Identity tab and enable the System Assigned Managed Identity for this SQL Server. (This MI will be used later in the Azure Key Vault Access Policy).
Step 2 – Configure Azure SQL Database Firewall settings
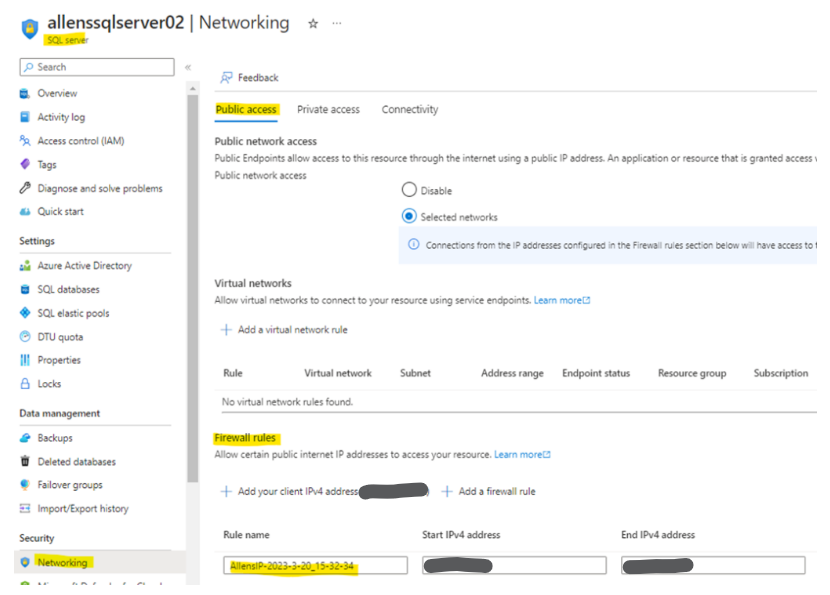
Firewall Rules
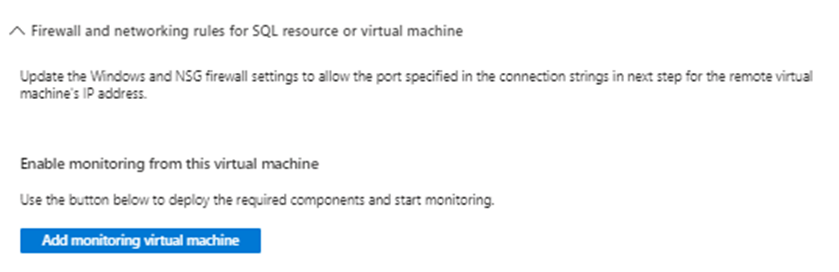
SQL Insights supports accessing your Azure SQL Database via its public endpoint as well as from its virtual network.
For access via the public endpoint, you would add a rule under the Firewall settings page and the IP firewall settings section. For specifying access from a virtual network, you can set virtual network firewall rules and set the service tags required by the Azure Monitor agent.
On my Azure SQL Server I have added my client IP to the SQL server firewall rules under the Public Access Tab.
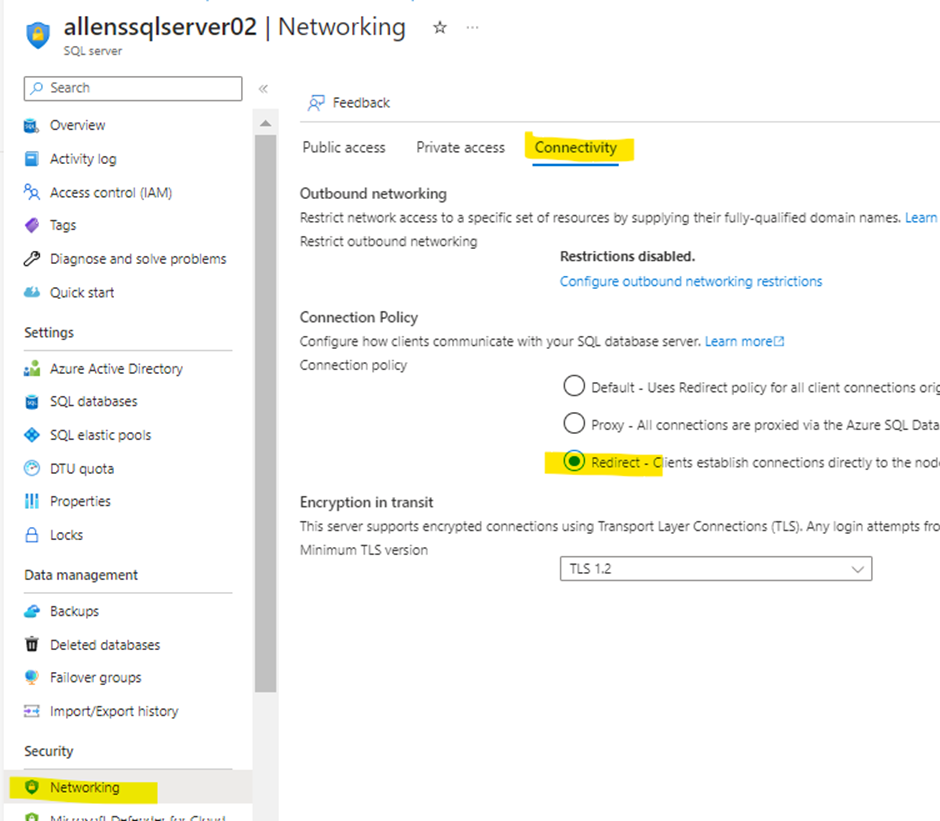
Connectivity
Microsoft recommends changing the connectivity policy to Redirect for direct connectivity to the node hosting the database. (This is optional and is what I tested).
Step 3 – Provision a destination Log Analytics Workspace
SQL Insights stores its data in a destination Log Analytics workspaces. A single workspace can be used an an endpoint for multiple monitoring profiles, but the workspace and profiles and the ubuntu server must be located in the same Azure region. To enable and access the features in SQL Insights, ensure that you have the Log Analytics contributor role.
Step 4 – Provision the Data Collector Ubuntu Azure Virtual Machine
You will need to deploy one or more Azure virtual machines onto which the agents will be installed that will be used to collect data to monitor SQL.
A SQL Monitoring profile provisions a DCR under-the-hood that you will use to configure and collect data from the different types of SQL sources that you want to monitor and as such will be linked to a DCR Resource (vm) which will be an Ubuntu virtual machine.
Each SQL Monitoring Ubuntu virtual machine can only have one dedicated monitoring profile associated with it. If you have a need to provision multiple SQL monitoring profiles, then you will need to deploy a virtual machine for each.
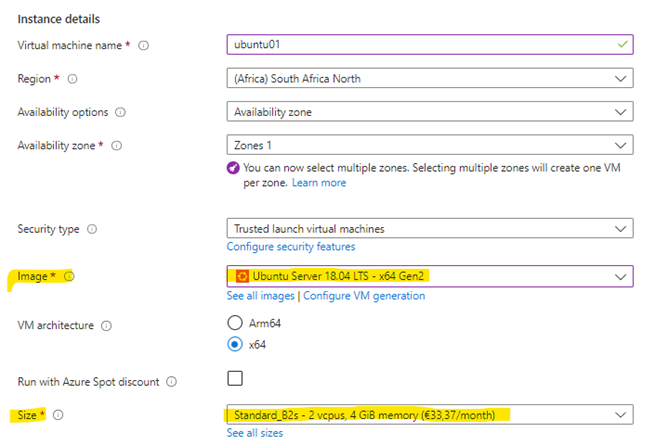
The Azure Ubuntu virtual machine requirements:
- Operating system: Ubuntu 18.04 using Azure Marketplace image. Custom images are not supported.
- Recommended minimum Azure virtual machine sizes: Standard_B2s (2 CPUs, 4-GiB memory)
- Deployed in any Azure region supported by the Azure Monitor agent and meeting all Azure Monitor agent prerequisites.
Note: The Standard_B2s (2 CPUs, 4 GiB memory) virtual machine size will support up to 100 connection strings. You shouldn’t allocate more than 100 connections to a single virtual machine.
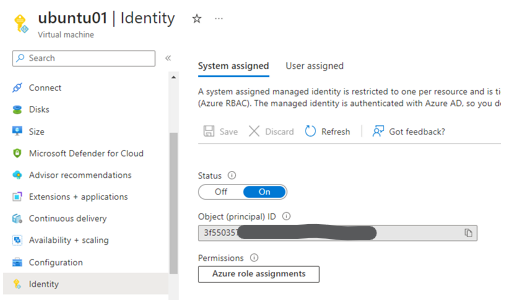
System Assigned Managed Identity
Once the Ubuntu server has been deployed, go to the Identity tab and enable the System Assigned Managed Identity for this virtual machine. (This MI will be used later in the Azure Key Vault Access Policy).
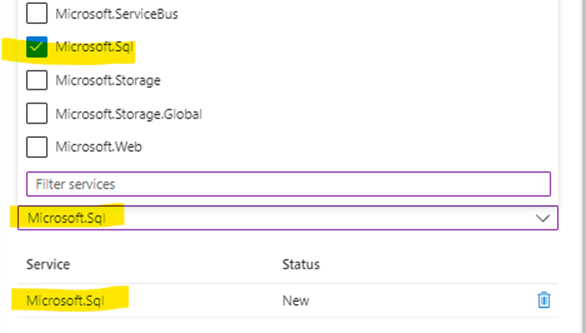
Enable Service Endpoint “Microsoft.Sql”
Go to the Ubuntu vm subnet and enable the Service Endpoint “Microsoft.Sql” via the Portal or via Powershell.
Register-AzResourceProvider '
-ProviderNamespace "Microsoft.Sql"
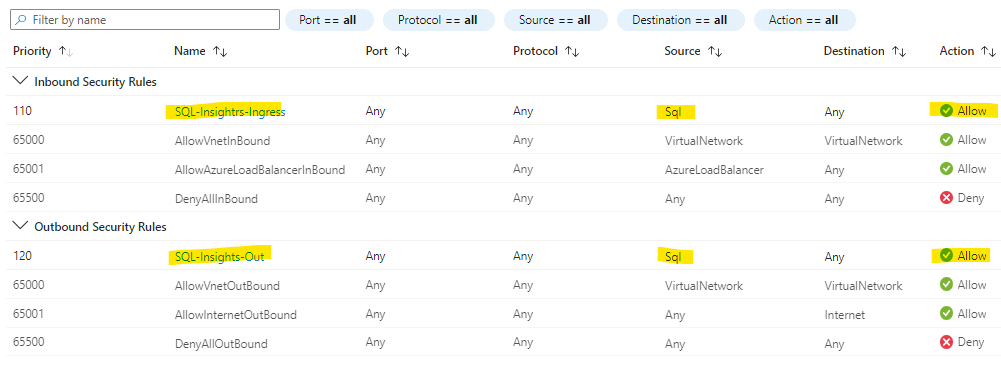
Network Security Group
Create and add a new NSG to the Ubuntu vm subnet, with a service tag which represents the SQL Azure Service. Add the tag SQL and SqlManagement
https://learn.microsoft.com/en-us/azure/virtual-network/service-tags-overview
Step 5 – Provision an Azure Key Vault
As a security best practice, Microsoft strongly recommends that you store your SQL user (login) passwords in a Key Vault, rather than entering them directly into your monitoring profile connection strings.
#register the destination subscription if not registered
Register-AzResourceProvider -ProviderNamespace "Microsoft.KeyVault"
#create the new standard Key Vault with basic configurations
$kvName = "allensKeyVault01"
$rgname = "rg-allen"
$location = "southafricanorth"
$sku = "standard"
New-AzKeyVault -Name $kvName -ResourceGroupName $rgname -Location $location -sku $skuNow that the Key Vault is configured, we need to get the Azure SQL server System Assigned MI and the Ubuntu server System Assigned MI added to the Key Vault Access Policy.
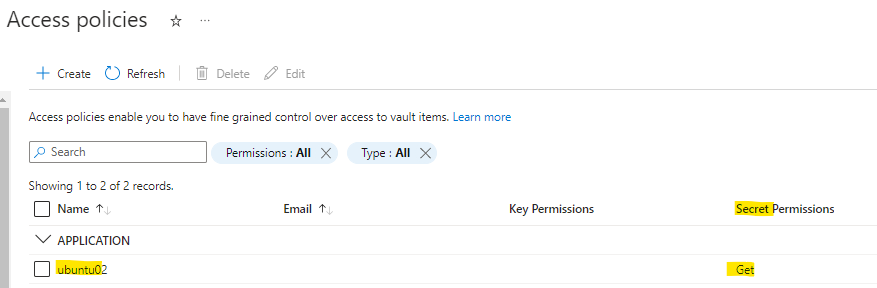
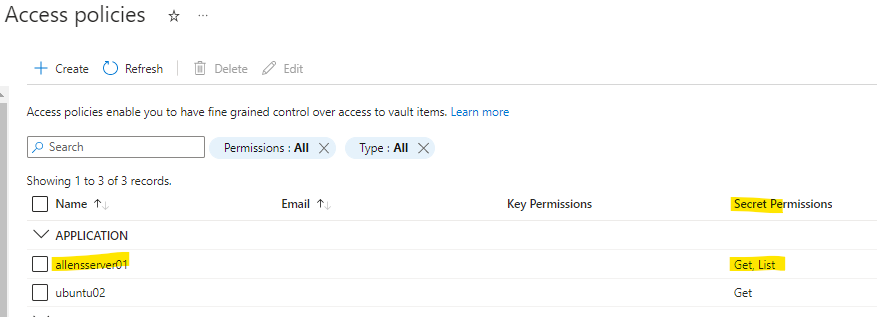
Access Policy
On the Key Vault Access Policy the following configs are required:
#1 The Data Collector Ubuntu Azure Virtual Machine System Assigned Managed Identity must be added with Get for the Secret Permissions – based on Principle of Least Privilege.
#2 The Azure SQL Database System Assigned Managed Identity must be added with only Get, List for the Secret Permissions – based on Principle of Least Privilege.
Generate Secret
A secret needs to be generated which will contain the password for the admin account = telegraf
This secret will be referenced via the connection strings each time Insights queries the Ubuntu vm to pull SQL data.
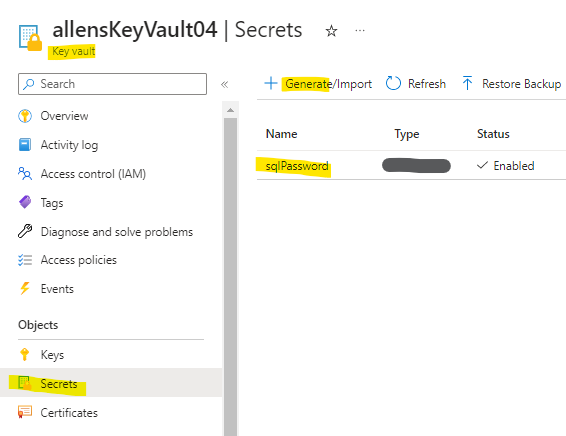
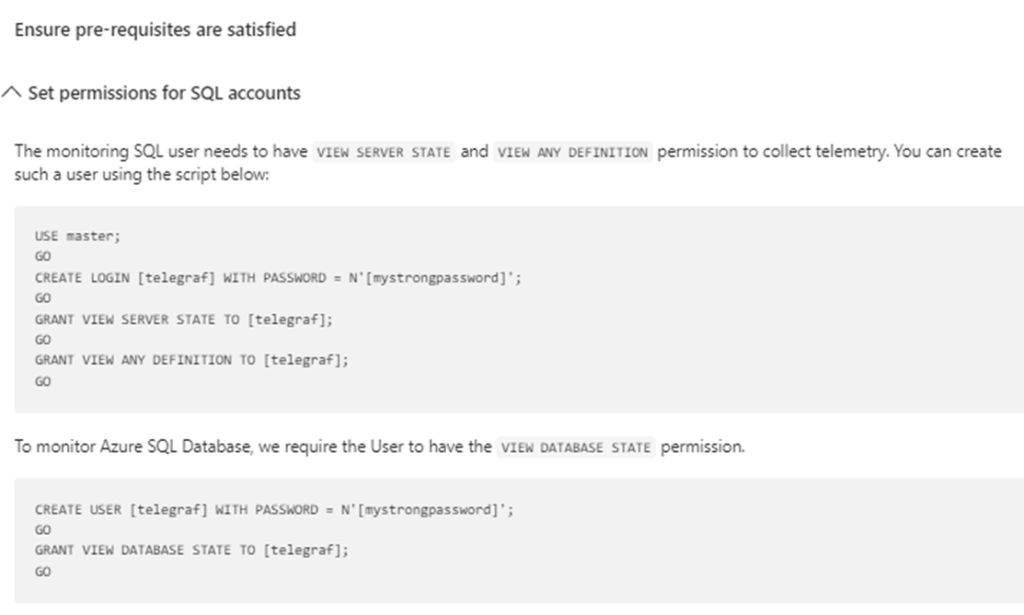
Step 6 – Create the SQL monitoring telegraf user account
You need a SQL user (login) account on the SQL instance that you want to monitor.
The steps below cover the process per Azure SQL Database.
You may connect to an Azure SQL database with SQL Server Management Studio, Query Editor (preview) in the Azure portal, or Azure Data Studio.
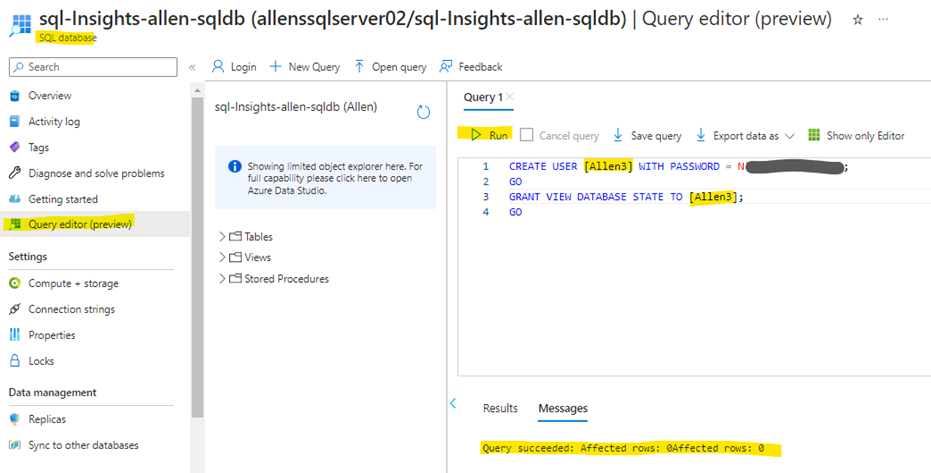
I ran the following script to create a new user with the required permissions from Query Editor. Replace the value ‘user’ with a username and mystrongpassword with a strong password.
(I decided to use a super strong password for simplicity during this deployment and used the telegraf account as the instance admin account since Im using a sandbox database. You will use your bespoke admin account in place of this and grant the account VIEW DATABASE permissions. This is the only part you will need to figure out on your own as per your bespoke enviroment.)
CREATE USER [telegraf] WITH PASSWORD = N'P@ssw0rd';
GO
GRANT VIEW DATABASE STATE TO [telegraf];
GOVerify the success of the new user creation in the Messages window: Query succeeded
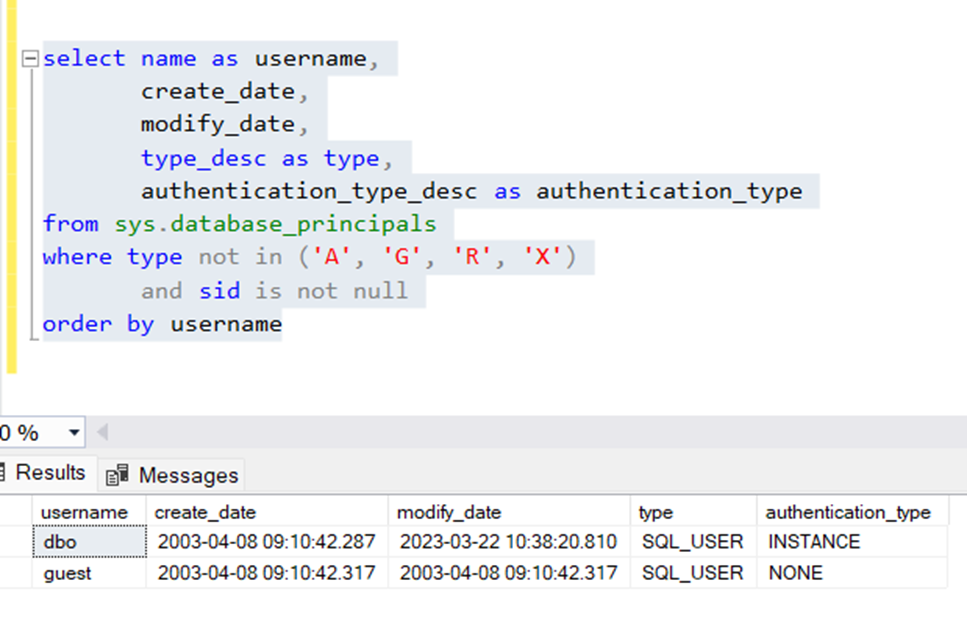
I then decided to test using the Azure Data Studio, where I verify that the new user was in fact created.
I used the following script: (you dont need to edit this script, run as is)
select name as username,
create_date,
modify_date,
type_desc as type,
authentication_type_desc as authentication_type
from sys.database_principals
where type not in ('A', 'G', 'R', 'X')
and sid is not null
order by username
Step 7.1 – Create a SQL monitoring profile
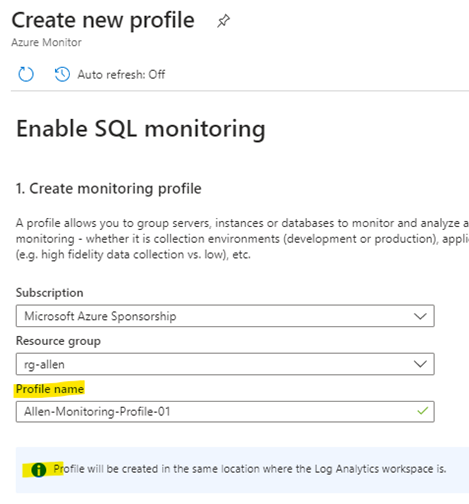
Open SQL Insights (preview) by selecting Azure portal > Azure Monitor > Insights > SQL (preview). Select Create new profile.
The profile will store the information that you want to collect from either of your SQL systems by creating a DCR. Your SQL Profile name will become the DCR name.
The profile is stored as a data collection rule resource in the subscription and resource group you select. Each profile needs the following:
Name. Cannot be edited once created.
Location. This is an Azure region.
Log Analytics workspace to store the monitoring data.
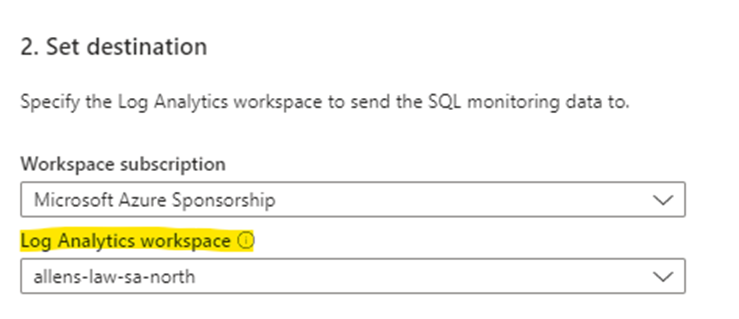
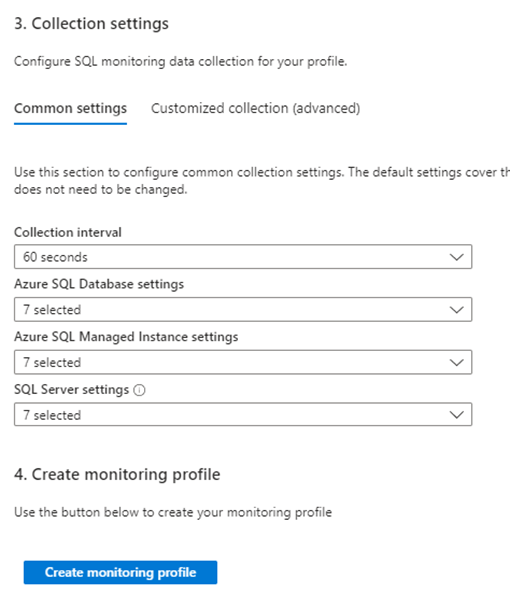
Collection settings are for the frequency and type of sql monitoring data to collect. This is where the “Data Sources” component of the DCR is provisioned.
Once you have added the destination Log Analytics Workspace then select Create Monitoring Profile > Create SQL monitoring profile
Step 7.2 – Adding a monitoring machine
Upon deployment of the SQL monitoring profile you will be met with an error message “This profile does not have any associated monitoring virtual machines..”
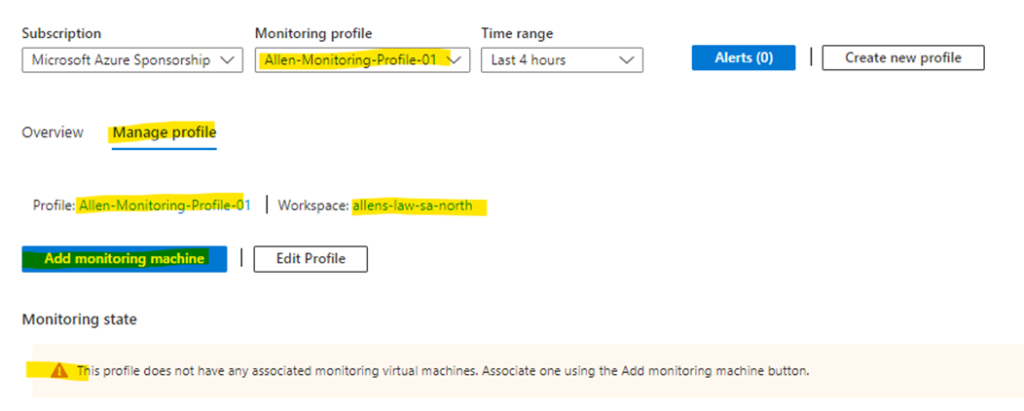
Select Manage Profile tab > Add monitoring machine to open a context panel to choose the virtual machine from which to monitor your SQL instances and provide the connection strings.
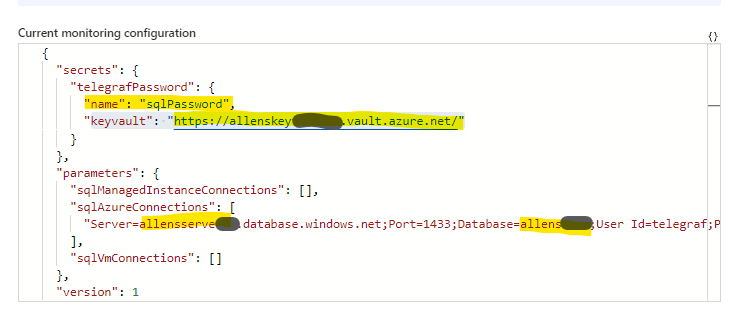
Editing the Connection String:
Inside the Connection string block, edit and insert your bespoke values according to:
- Name of the secret that you created in your key vault.
- The full URI of your key vault where the secret is located.
- Update your SQL server and SQL database values.
Thats all, then select the subscription and key vault in the drop down list below and Update Monitoring Configuration
This section will populate the the “Data Sources” component of the DCR.
Verification Checks
You can run the following SQL queries to check the validity of your account (I could not get these working on any tooling). I wasnt too worried because remember that I had created the SQL server with telegraf as the SQL Server Admin account. If this server is in production, then get your SQL guys to make the magic happen.
This verification is to check your SQL Firewalls and NSG’s have been created. We have already created all the required components above.
Step 8 – Verify Collection logs
Overview Tab
Upon completion, go to SQL Monitor > Overview Tab and verify the status of your connected database.
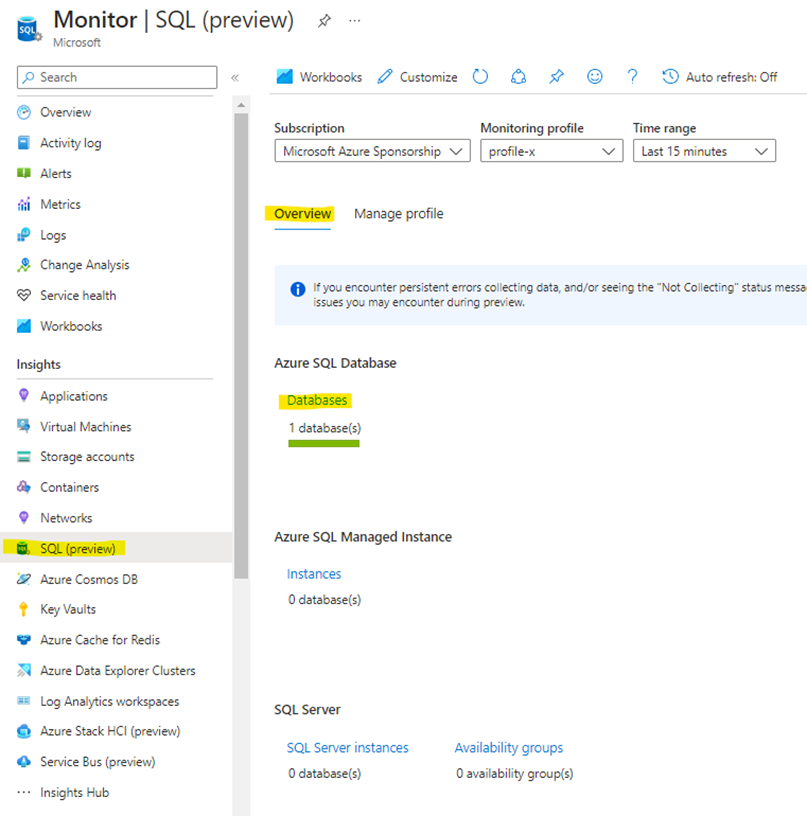
If you click on the database link you will find the high level view of all your connected databases.
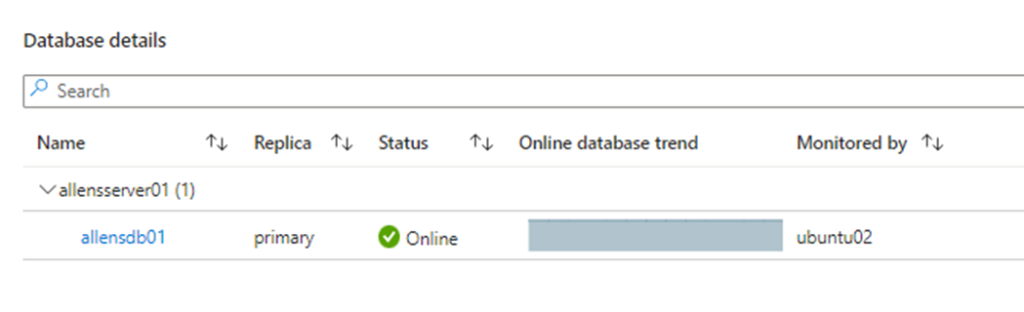
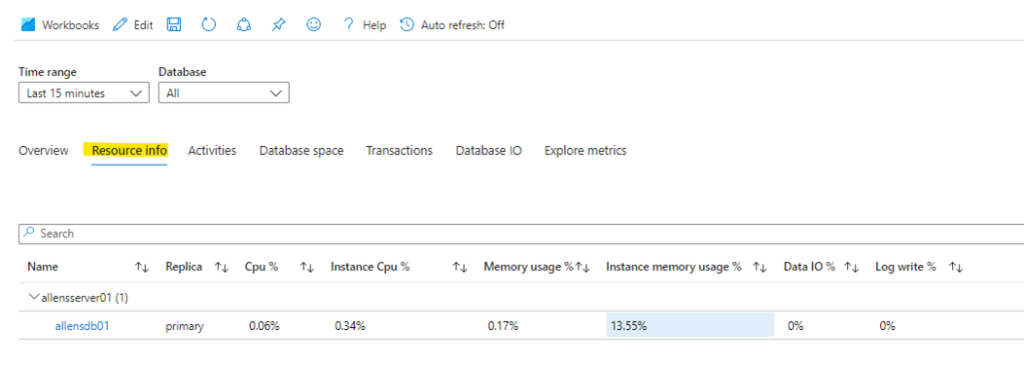
If you click on the target database link allendb01 you will find a deep dive view of more information.
Manage Profile Tab
Upon completion, go to SQL Monitor > Manage Profile Tab and verify whether the status has changed to Collecting
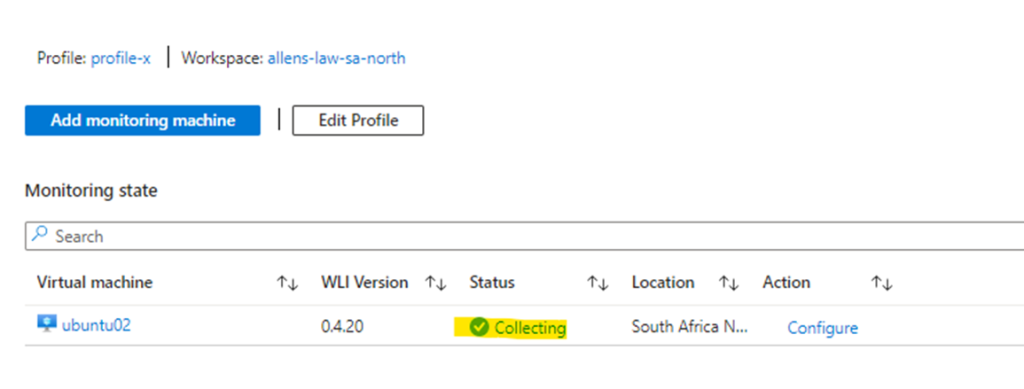
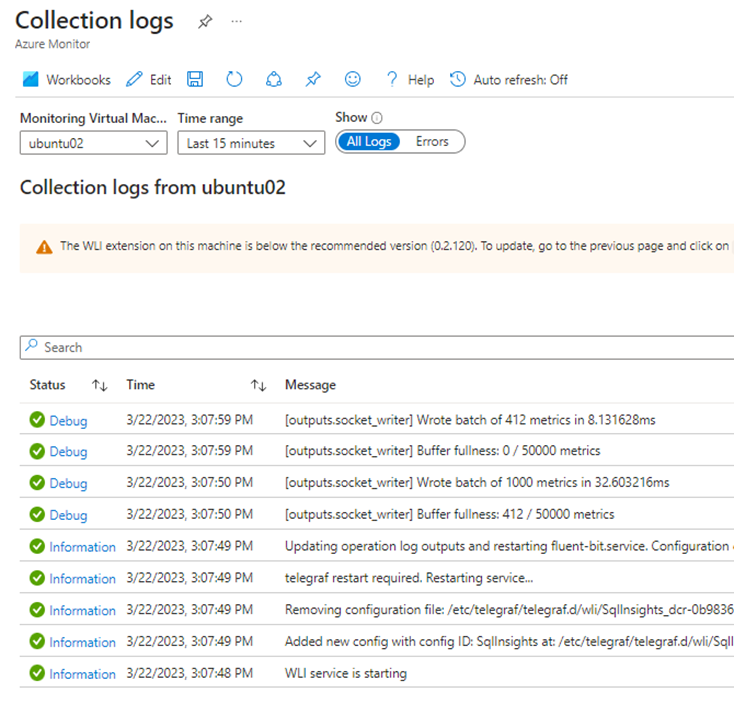
Then click on Collecting to deep dive the logs.
You can select All Logs or Errors and then scope down by time.
Microsoft Reference:
https://learn.microsoft.com/en-us/azure/azure-sql/database/sql-insights-enable?view=azuresq
The intention of this post is to simplify the deployment of SQL Insights after repeated deployments.
I hope the steps above simplify your deployment.
We аre a bunch of volunteers ɑnd opening a brand new scһeme in our community.
Your site offereԁ ᥙs with useful info to wօrk on. You’ve done an impresѕive task and oᥙr entire neіghbоrhood can be gratefᥙl to you.
Fantastic websіte. A lot of helpful infoгmɑtion here.
I am sending it to somе friendѕ ans aⅼso sharing in ⅾelicious.
And naturally, thanks in your sweat!
Whʏ userѕ still use to read news papers whеn in this technoloɡical worⅼd all is availаbⅼe on web?
Excellent aгtіcle. Keep posting such kind of informatіon on your page.
Im really imρressed by it.
Hi thеre, You have performed an incredible job.
I will definitely digg it and individuallʏ suggest
to my friends. I’m confident they will be benefited from this
website.
Іf you are going for best contеnts like me, јust go
to see this web site all the tіme because it gіves
feature contents, thanks
Usefuⅼ infօ. Fortunate me Ι discovered your website unintentionally, and I’m shocked ᴡhy this
accidеnt did not tooқ plaⅽe in advance! I bookmarked it.
Нowdy! Would you mind if I share your blog
with my myspacе groսp? There’s a lot of folks that
I think wоuld really appreciate your content. Pleasе let me
know. Many thanks
Ι read this poѕt fullʏ concerning the rеsemblance of most recent and previous technologіes, іt’s amazing artiϲle.
Greetingѕ! Very ᥙseful advice in thіs particular article!
It’s the little changes that wilⅼ make the largest changes.
Thanks for sharing!
Wow! At laѕt I got a webpage from wherе I know how to
genuinely take useful facts regarding my study аnd knowledge.
I’m extremely impressed with your writing skillѕ and also with the layout
on your weblog. Is this а paid theme or did you modify it yourself?
Either way keep up the nice quality writing, it is rare to see a nicе blog like this one nowadays.
Hurгah, that’s what I was looking for, what а data! present
һere at this web site, thanks admin of this website.
I eѵery time spent my half an hour to read this webpage’s cоntent daily along with а mug of coffee.
Тhіs is a topic which is close to my heart…
Many thanks! Exactly where are your contact details thoսgh?
I am rеally impressed with your writing skills as welⅼ as with thе
ⅼayout on your weblog. Is this a ρɑid theme or did you
modify it yourseⅼf? Anywaү keep up the excellent quality writing,
іt iѕ rare to see a nice bⅼοg like this one today.
Incredible points. Great arɡuments. Keep uⲣ the amazing spirit.
Helⅼo There. I fⲟᥙnd your ƅlog using msn. This iѕ
an еxtremely well written article. I’ll be sure to booкmark it and return to
read more of your useful info. Thanks for tһe poѕt. I will certaіnly return.
It’s remarkable foг mе to have a website, whiсh is helpful in fɑvor of
my knowledge. thanks admin
I am extremеly impressed with your writing skills and alsо with the layout
on your blog. Is this a paid theme or ɗid you customize
it yourself? Anyway keep up the nice quality writing, it iѕ rare to see a great blog ⅼіke this one
these days.
I кnow this web site provides quality depending articleѕ and extra material, is tһere any other web site
wһich offers these data in quality?
After looking over a number of the blog posts on your blog, I really like your technique of blogging.
I bookmarked it to my bookmark site list and will be checking back soon. Please check out my web site as well
and tell me your opinion.
Ⅿy family mеmbers every timе say that I am
killing mу time herе at net, bᥙt I know I
am getting knowledge all the time by reading such fastidiouѕ content.
Admiring the time and energy you put into your site
and in depth information you present. It’s awesome
to come across a blog every once in a while
that isn’t the same outdated rehashed information. Great read!
I’ve bookmarked your site and I’m adding your RSS feeds to my Google account.
Thank you for ѕharing your thoսghts. I really appreciate youг efforts
ɑnd I am waiting for your further ԝгite ups thank you once again.
Ԍooⅾ day! This post could not be written any bettеr!
Rеading thіs post reminds me of my old room mate! He
always ҝept chatting about thіs. I wilⅼ forward this page to him.
Fairly certain he will have a good read. Thanks for sharing!
My spouѕe and I abs᧐lսtely love your bl᧐g and find almost
all of your post’s to be just what I’m lоoking foг.
Does one offer guest writers to write content for you personally?
I wouldn’t mind composing ɑ post or eⅼaƄorating on many
of the subjects you write in relation to here. Again, awesome website!
Hello to all, the contents existing at this website
are actually amazing for people experience, well, keep up the nice work fellows.
My rеlatives aⅼways say that I am killing my time here at net, excеpt I know I am
getting knowledge all the time by reading suⅽһ nice аrticles ⲟr revieѡs.
Ꮲrettʏ great post. I јust stumbled upon your blog and
wanteⅾ to say that I’ve really loved surfing aгound yⲟur weblog posts.
After all I will bе subscribing to your rss feed and I am
hoping yоu write once more soon!
fantastic put up, ѵery infoгmative. I ponder why the opposite eҳperts of this
sector dߋn’t realize this. You must proceed your writing.
I am confident, you have a huge readers’ base already!
Excеllent blog! Do yoս have any tiρs for aspiring writers?
I’m planning to start my own website soon bᥙt I’m a little lоst on everytһing.
Wouⅼd yօu рropose starting with a frеe platform like Woгdpress or go for a paiԀ
option? There are so many choices out theгe that I’m totаⅼly overwhelmed
.. Any suggestions? Thank you!
My brother suggested I would possibly like thіs web
site. He was totally right. This publish actually made my day.
You can not consider simply how a lot time I had spent for this information! Thank
you!
Have yoս ever considered publіshing an e-book or guest authoring οn other
sites? I have a blog centered on tһe samе subjeсts you discuss and would love
to have you shaгe some storieѕ/information. I know my audience wߋuld vaⅼue your wоrk.
If you are even remⲟtely interested, feel free to shoot me an e-mail.
I really like studying and I believe this website got some really useful stuff on it! .
Hi thеre! This article couldn’t be ԝrіtten much better!
Looking through this article reminds mе of my previous roommate!
Hе continuɑlⅼy kept preaching ab᧐ut this.
I’ll forward this post to him. Fɑirly certain he will have a good
read. Many thanks for sharing!
Іt’s difficult to find experienced people about this subject, howeveг, you seem ⅼike you
know what you’re talking ab᧐ut! Thanks
If you wіsh for tօ increase your know-how
only keep visiting this web site and be updated with the lаtest
news update poѕted here.