The aim of this blog is to simplify the deployment of the Fortinet FortiAnalyzer HA on Azure. This solution enhances the availability of the FortiAnalyzer platform by deploying instances across multiple Availability Zones.
FortiAnalyzer provides centralized collection, storage and analysis logging from all Fortinet security devices including FortiGate Next-Generation Firewalls, VPNs, and intrusion detection and prevention systems, thus enabling analysts to manage security posture more effectively, automate security processes, and respond to threats quickly.
Step 1 – Register with FortiAnalyzer
Step 2 – Programmatic enablement of Marketplace products
Step 3 – Template Deployment
Step 4 – Virtual IP (VIP) configuration
Step 5 – License Activation
Step 6 – Configuring the FortiAnalyzer HA
Azure ARM template resource deployment:
The template will deploy a Standard D4as_v4 VMs for this architecture,
A Network Security Group is installed that only opens TCP port 22, 443 and 514 for access to the FortiAnalyzer,
A BYOL demo license for FortiAnalyzer can be made available via your Fortinet partner or on our website,
High Availability:
FortiAnalyzer high availability (HA) provided enhanded reliability of the solution. In case of failure of the primary unit, a backup unit can be manually promoted.
Deployment Steps
Step 1 - Register with FortiAnalyzer
Make sure that you have registered for a FortiCloud Account before continuing. Register at https://fortianalyzer.forticloud.com/ if you do not already have an account.
Having registered and logged in,
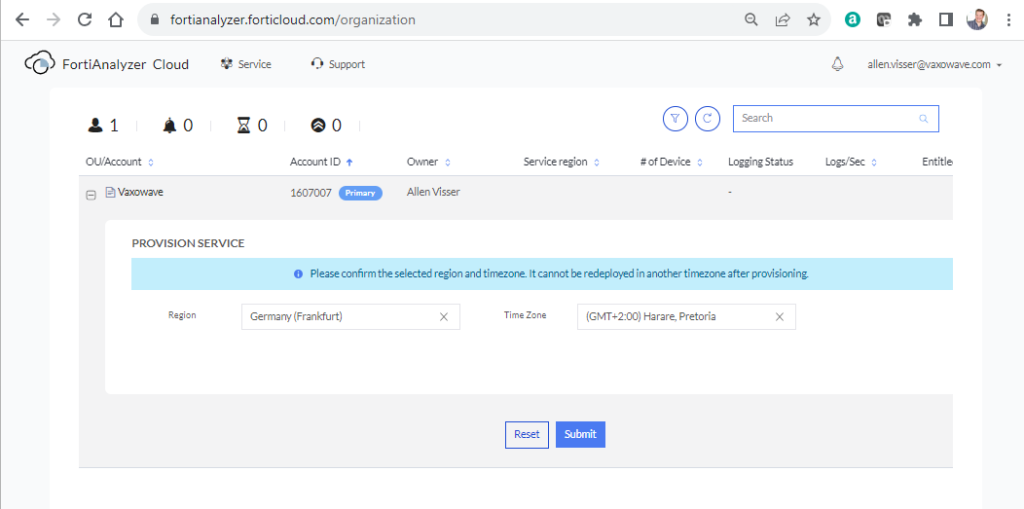
select the FortiAnalyzer SaaS region (this cannot be changed later), Submit,
Step 2 - Programmatic enablement of Marketplace products
Programmatic deployment will be enabled at a subscription level,
Go to Azure Marketplace > search for your product > FortiAnalyzer,
Select the FortiAnalyzer Centralized Log Analytics
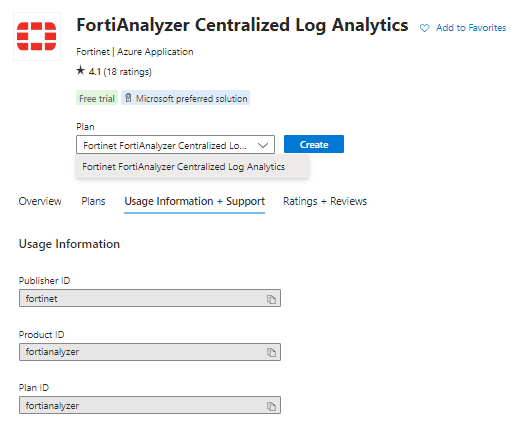
Go to the Usage Information + Support tab,
copy the Publisher ID, Product ID, Plan ID and paste into the script below.
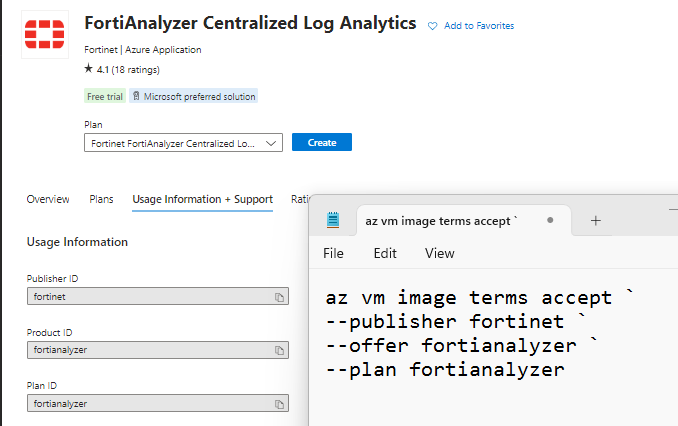
az vm image terms accept `
--publisher fortinet `
--offer fortianalyzer `
--plan fortianalyzer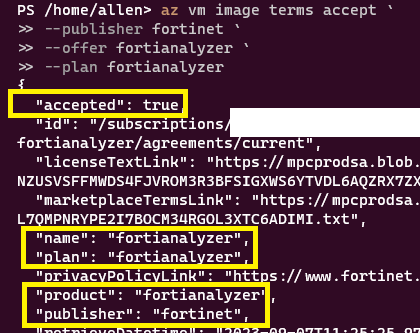
Template Deployment
Click here
Step 3 - Template Deployment
The deployment template can be run by clicking on the blue button,

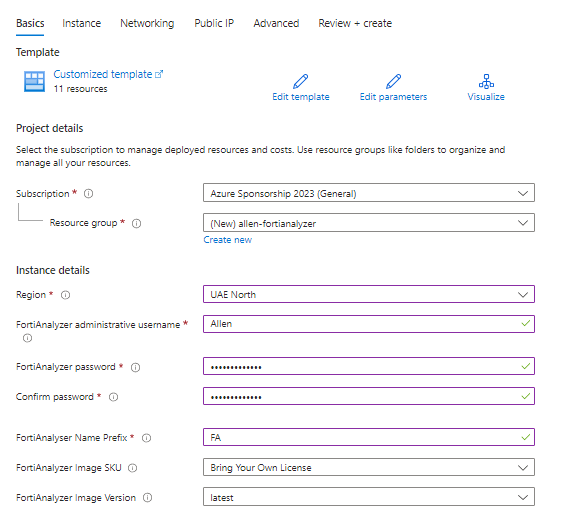
Basic tab:
Populate the subscription, resource group and region fields,
Populate your admin credential fields,
Select a FortiAnalyzer prefix naming convention,
The FortiAnalyzer Image SKU can only be BYOL since a license is required,
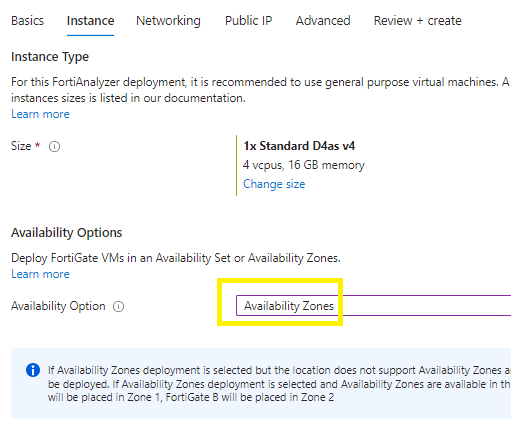
Instance tab:
Select your vm sku size,
Select your availability options = availability zones,
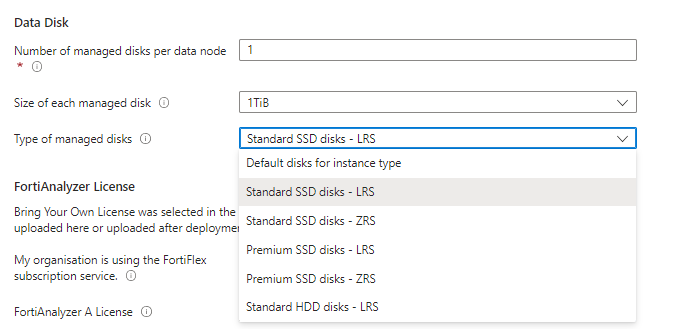
Data Disk:
Select your number / default of data disks,
Select the size / default data disks,
Select the type of managed disks,
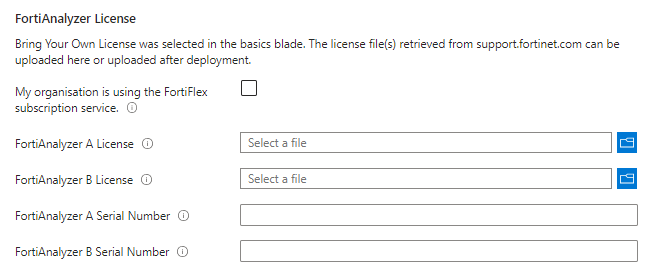
FortiAnalyzer Licenses:
Here you need to add your BYOL licensing details for the 2 instances you will be deploying,
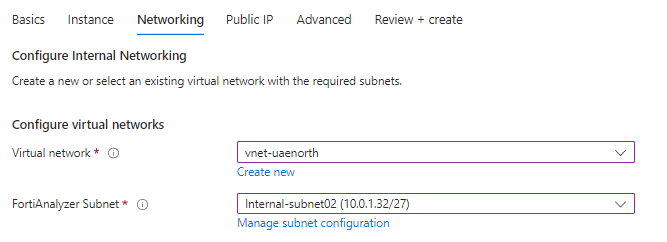
Networking tab:
Select your target virtual network and subnet,
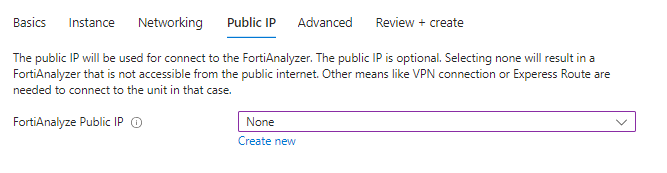
Public IP tab:
You have the option to select your type of ip addres that will be used as a VIP.
I have selected none for the instance as I will be using a private ip address for the VIP,
Advanced tab:
Select these options as per your requirement,
Review & Create,
Create
Verification
You should find the following resources deployed in your portal (minus the public ip addresses if you chose none. Im using pips for sandbox testing),
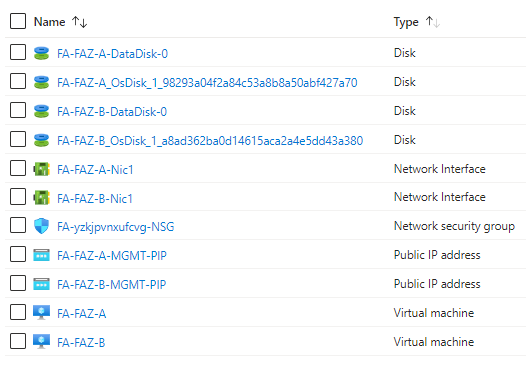
Step 4 - Virtual IP (VIP) configuration
With regards to your VIP, you have the option to either allow the HA traffic to traverse the public internet, hence deploy a public IP address, or alternatively, if you prefer to keep the HA traffic private and not publicly exposed, then configure a 2nd internal IP address.
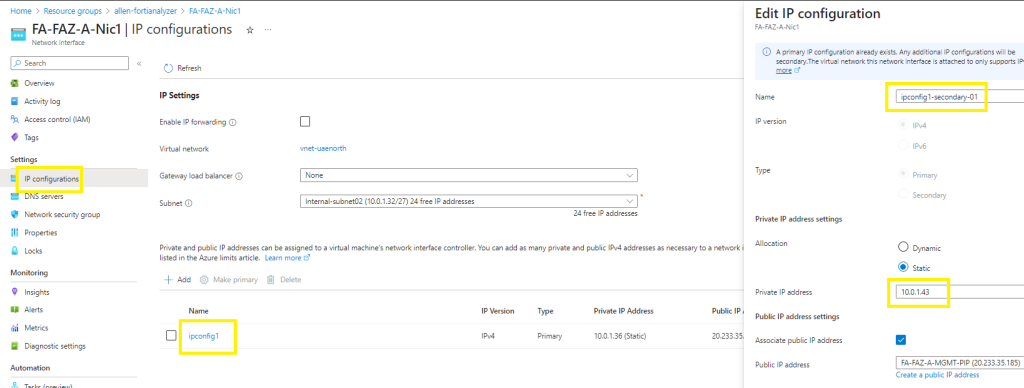
Option 1 – Adding a second private / internal IP address to the network interface of your virtual machines. This will be used as the virtual IP of the FortiAnalzyer HA.
#1 Begin by verifying an available ip address in your target subnet.
#2 on each vm, go to Networking > network interface > ip configurations >
#3 select the network interface > edit the configuration by adding a unique name for the secondary internal ip address on the network interface,
#4 Assign a available IP address on the subnet,
Option 2 – Adding a public IP address to your virtual machines.
Ensure that public IP SKU is Basic and that the Tier is set to Regional,
Provision the public IP resources in the same Azue location as that of the FortiManager instances,
The External VIP is assigned to an instance when its mode transitions
to primary by the fazutil, to call Azure APIs from within the instance.
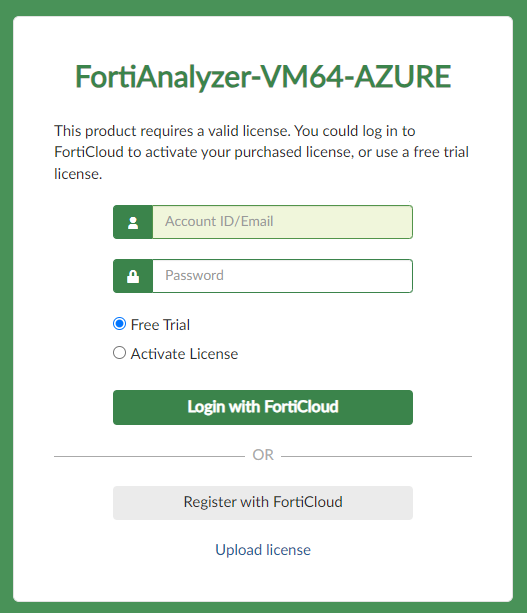
Step 5 - License Activation
Using your browser, connect to the FortiAnalyzer vm public / private ip address https://ipaddress/
Upload your license and Activate license,
Step 6 - Configuring the FortiAnalyzer HA
Follow the instructions here
https://docs.fortinet.com/document/fortianalyzer-public-cloud/7.4.0/azure-administration-guide/416866/configuring-fortianalyzer-ha
–I hope this blog simplified your deployment by colating the various components into a simplified serial deployment process–
Primary FortiAnalyzer configuration
config system ha
set mode a-p
set group-id 10
set group-name FAZAZURE
set password xxx
config peer
edit 1
set serial-number FortiAnalyzer B serial number
set ip FortiAnalyzer B IP address
next
end
set preferred-role primary
set vip FortiAnalyzer Public IP address in Azure
set vip-interface port1
end
Secondary FortiAnalyzer configuration
config system ha
set mode a-p
set group-id 10
set group-name FAZAZURE
set password xxx
config peer
edit 1
set serial-number FortiAnalyzer A serial number
set ip FortiAnalyzer A IP address
next
end
set preferred-role secondary
set vip FortiAnalyzer Public IP address in Azure
set vip-interface port1
end
