This post provides a simple sample to execute in your enviroment in order to verify whether you have correctly configured your Microsoft Defender for Cloud alerts.
Microsoft Defender for Cloud (MDC) Alerts are the notifications that Defender for Cloud generates when it detects threats on your resources. It prioritizes and lists the alerts along with the information needed to quickly investigate the problem. Defender for Cloud also provides recommendations for how you can remediate an attack.
The sample alerts will assist with 2 scenarios:
- evaluating the capabilities of your Microsoft Defender plans
- validate any configurations you’ve made for your security alerts and their integration into a SIEM solution such as Sentinel integration, workflow automation, and email notifications.
To create sample alerts to test the Microsoft Defender plans at a subscription level:
Required RBAC role: Subscription Contributor.
Deployment Steps: Portal > Microsoft Defender for Cloud > Security Alerts > Sample alerts
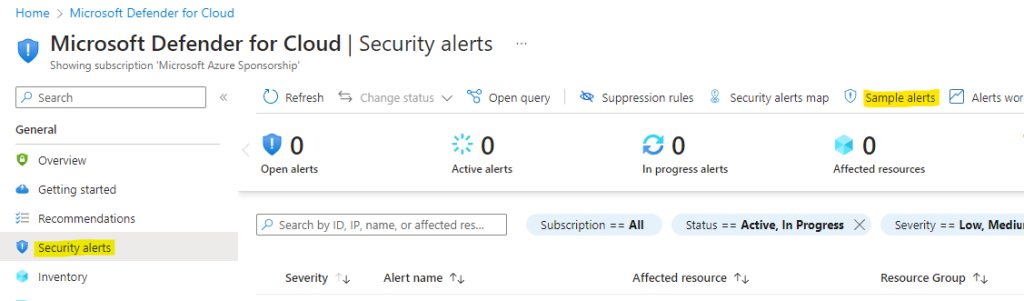
> select your target subscription > select the relevant Microsoft Defender plans for which you want to see alerts > Create sample alerts.
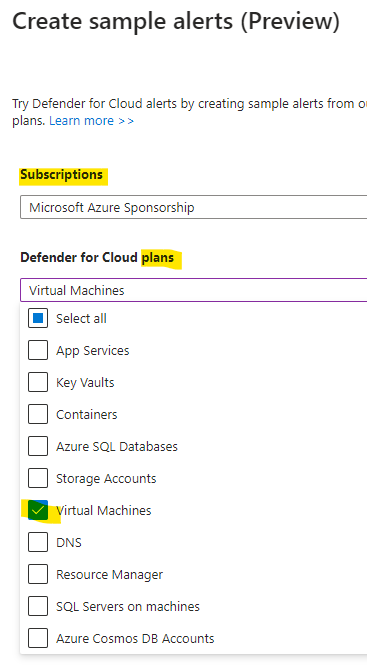
A notification appears letting you know that the sample alerts are being created
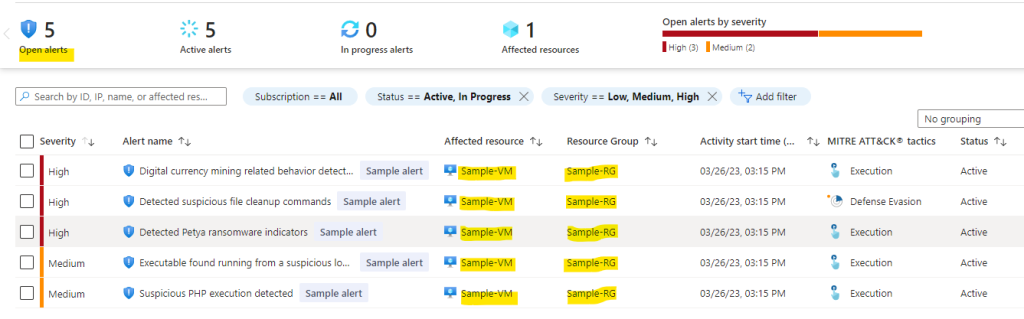
After a few minutes, the alerts appear in the security alerts page. They’ll also appear in any additional SIEM platformsthat you have connected to receive your Microsoft Defender for Cloud security alerts (connected SIEMs, email notifications, and so on).
To create sample alerts to test the Microsoft Defender plans at a virtual machine instance level:
Deployment Steps:
- Make sure the vm you plan to run the sample test on has MDC enabled.
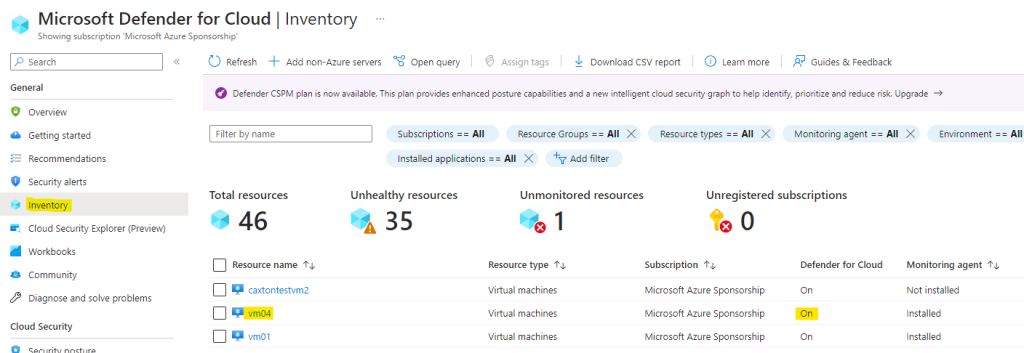
- Go to MDC > Inventory > select your vm > check the MDC column > ON
Logon to a vm in Azure (which must be protected by the Microsoft Defender for Cloud).
When reviewing this test alert for Windows, make sure the field Arguments Auditing Enabled is true. If it is false, then you need to enable command-line arguments auditing. To enable it, use the following command:
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\Audit" /f /v "ProcessCreationIncludeCmdLine_Enabled"
- Copy an executable (for example C:\Windows\System32\calc.exe) to the computer’s desktop, or a custom directory location, and rename it as MDC_AlertTest_calc.exe
- Open the command prompt and execute this file with an argument (just a fake argument name), such as:
MDC_AlertTest_calc.exe -foo - Wait 5 to 10 minutes and open Defender for Cloud Alerts. An alert should appear.
Microsoft Reference
https://learn.microsoft.com/en-us/azure/defender-for-cloud/alert-validation