This blog is written with the intent to easily and quickly configure availability testing on internal web app or website URL’s. Along with the Application Insights test, I have added optional verification and pro-active customizable alerting notifications.
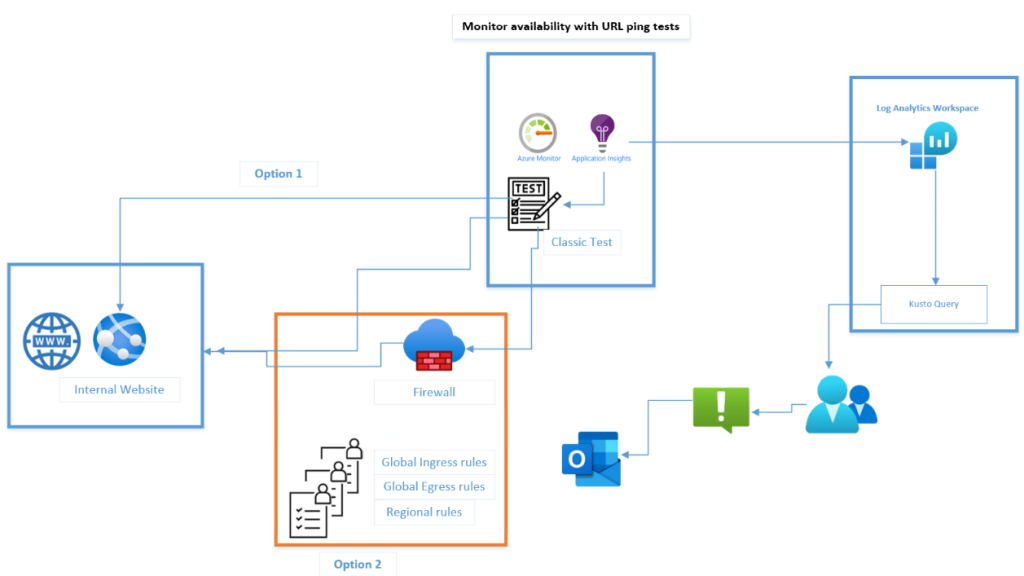
I have added 3 options in this walkthru:
Option 1 – URLs that are publicly exposed and can be monitored via Application Insights,
Option 2 – URLs that are not publicly exposed and can be monitored via Application Insights (which allow editing firewall rules),
Option 3 – URLs that are not publicly exposed and cannot be monitored by Applications Insights (which do not allow editing firewall rules).
Option 1 - URLs that are publicly exposed and can be monitored via Application Insights
Components:
- Log Analytics Workspace (destination endpoint)
- Application Insights resource
- Application Insights Test
Procedure
1. Log Analytics Workspace
a. Identify or create a destination LAW for your Application Insights
2. Application Insights
a. Sign in to the Azure portal and create your Application Insights resource
b. Select your pre-identified destination LAW > create
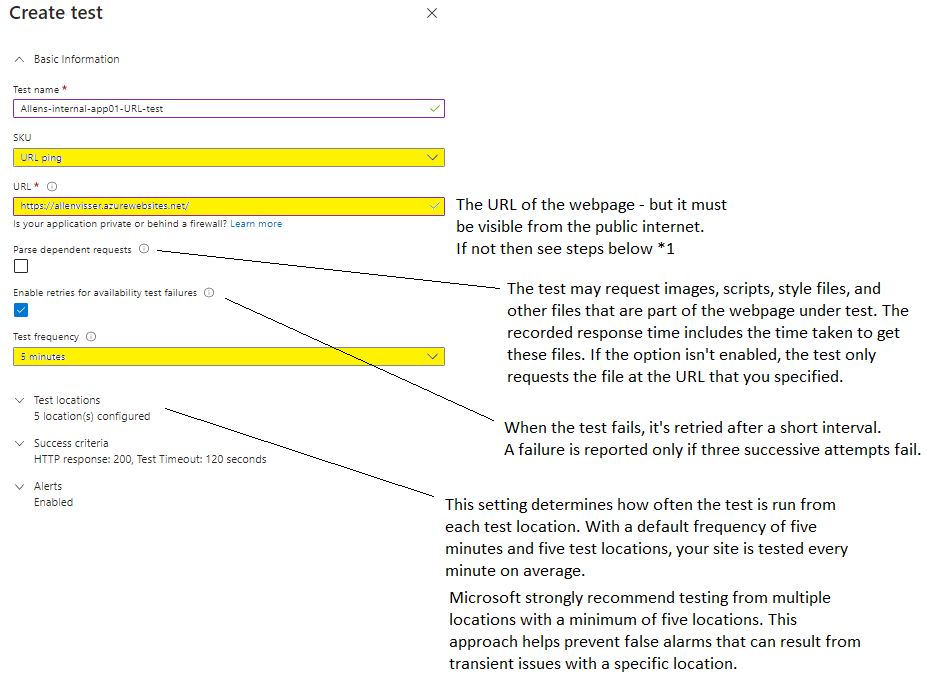
3. Create the Application Insights Classic Test
(The Classic Test simplifies testing instead of using the Standard Test if you don’t want to include negotiate SSL features in the test)
a. Application Insights resource > select Availability > select Add Classic Test
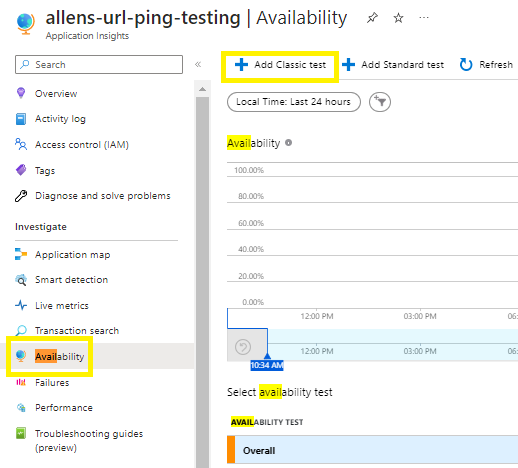
The URL represents the webpage that you want to test, but it must be visible from the public internet. If your URL isn’t visible from the public internet, you can choose to selectively open your firewall to allow only the test transactions through (which is explained in option 2).
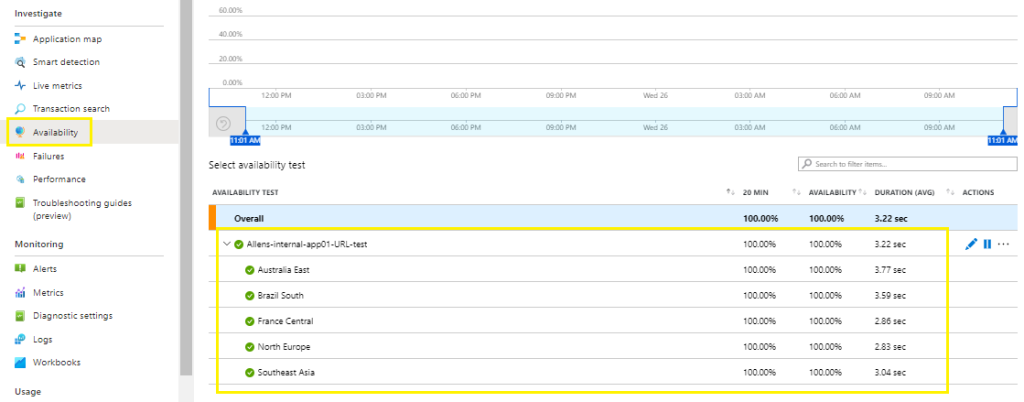
Verification
Select your Classic Test and view the results based on your defined frequency across the recommended 5 regions.
Alerting notifications
Let’s setup some proactive Azure Monitor Alerting by selecting View in Logs
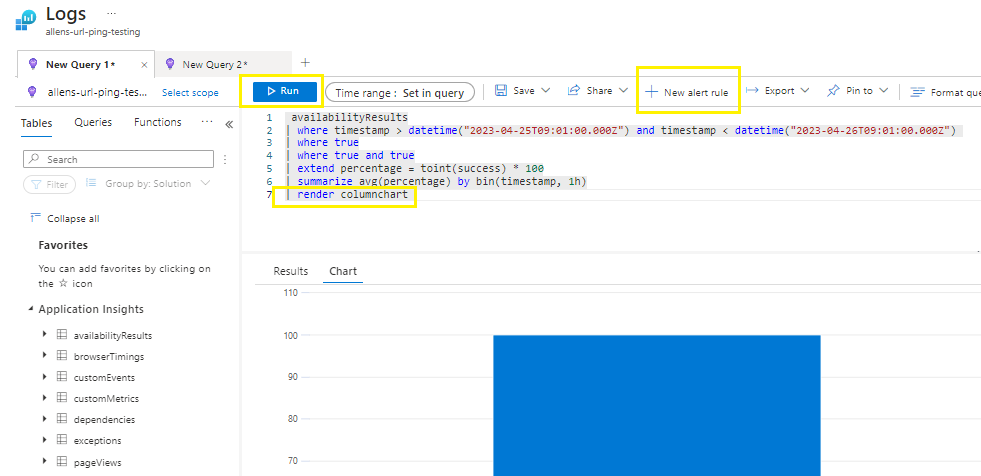
I changed my KQL to a | render columnchart > Run (to make sure you get the correct results)
When you are satisfied with the result > select New alert rule
Azure Monitor Alert
Scope tab:
Will be prepopulated based on the KQL query,
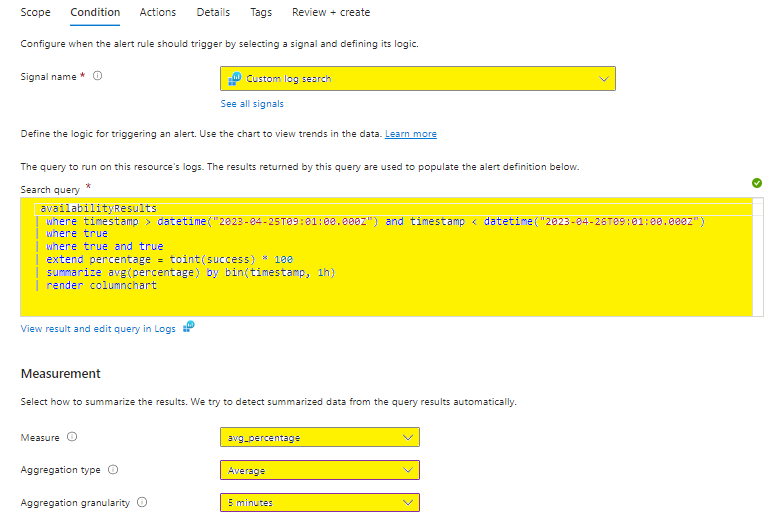
Condition tab:
The Signal name will automatically be Custom log search
The Search Query will be KQL query from the Logs
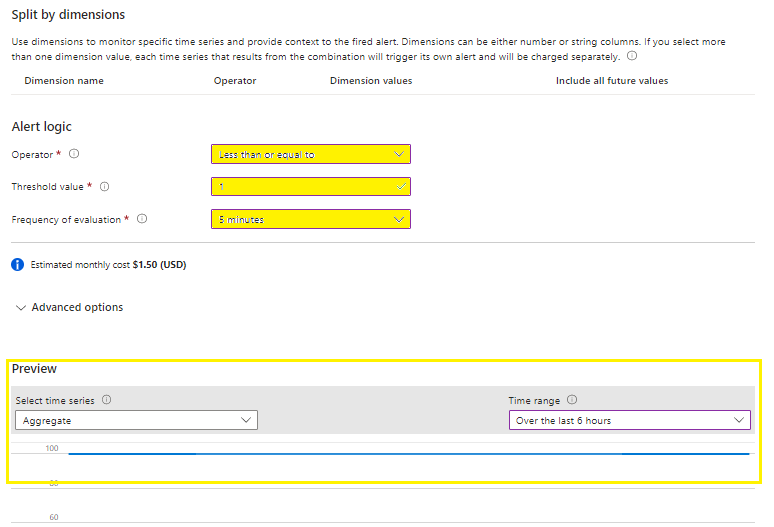
Select your bespoke Measurement conditions
Select your bespoke Alert logic conditions and review the preview for expected results.
Actions tab:
Create or select your Action Group that will receive the designated URL Ping Test failures,
Details tab:
Select the Severity Level of the alert,
Select a unique identifiable rule name and description,
Select the region,
Review and Create.
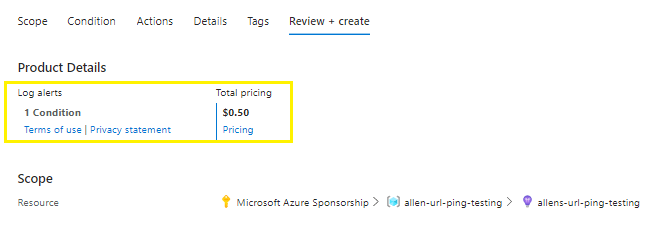
Costs
Always keep in mind that triggers and alerts are cost incurring and that these alerts will cost $0.50c per trigger.
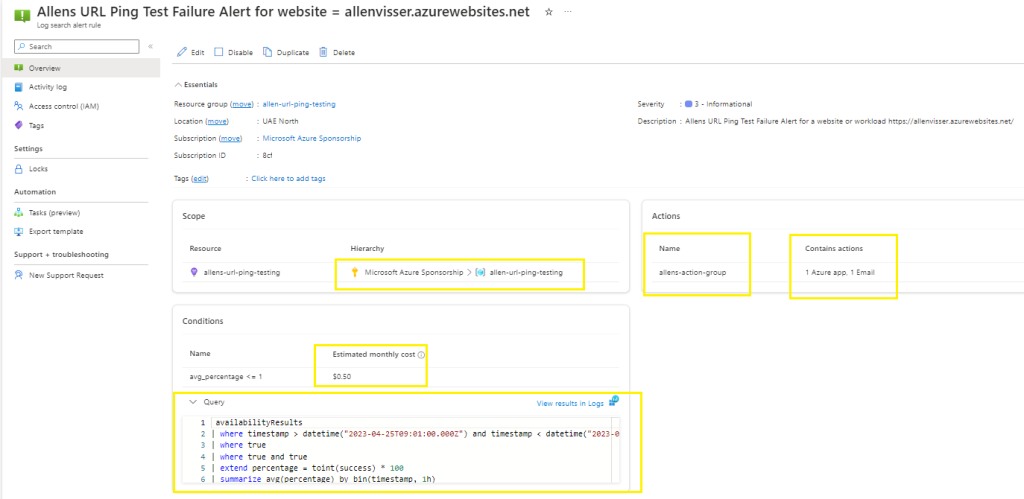
Moving over to Azure Monitor > Alerts > verify your configuration is correct.
Option 2 - URLs that are not publicly exposed that can be monitored via Application Insights (which allow editing of firewall rules)
- Editing of Azure based firewall rules
a. Add the Global IP Addresses for ingress traffic rules,
b. Add the Global IP Addresses for live metrics egress traffic rules,
c. Add the Regional IP Addresses ingress traffic rules, - Log Analytics Workspace
a. Identify or create a destination LAW for your Application Insights - Application Insights
a. Sign in to the Azure portal and create your Application Insights resource
b. Select your pre-identified destination LAW > create - Create the Application Insights Classic Test
(The Classic Test simplifies testing instead of the Standard Test if you don’t want to include SSL features in the test)
Application Insights resource > select Availability > select Add Classic Test
- Editing of Azure based firewall rules
If your URL isn’t visible from the public internet, you can choose to selectively open your firewall to allow only the test transactions traffic.
The Azure IP addresses are categorized by both, region and globally. You will have to easily combine both sets of information as per your region.
#1 Global IP Addresses (ingress):
If you’re looking to filter the specific IP addresses to add on your firewall ingress rules, then download the JSON file that describes the Azure IP ranges from https://www.microsoft.com/en-us/download/details.aspx?id=56519
The file contains the most up-to-date information of all Azure IPs. Open and search the JSON file for ApplicationInsightsAvailability to find the service tag for availability tests.
Grab all these IPs as the global ingress list. (Now lets add the global IP egress list)
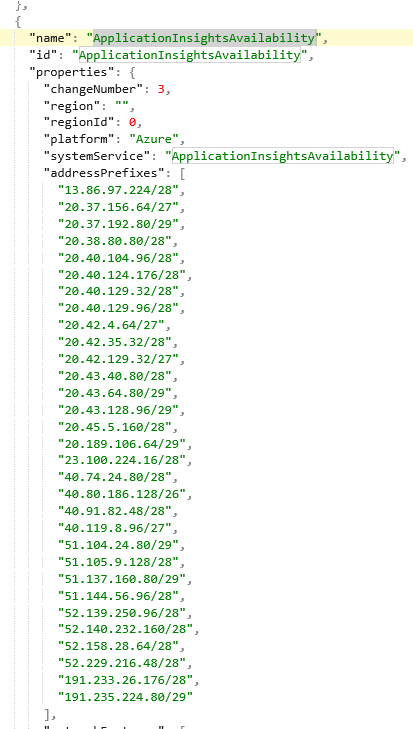
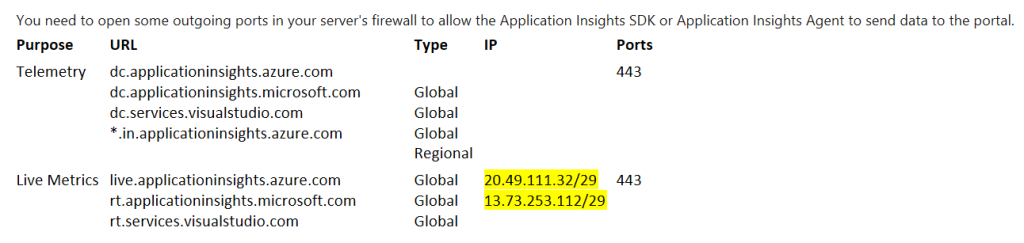
#2 Global IP Addresses (egress):
Merely add the following ips for the global egress IPs (which is required for live metrics) as per the insert below. (This completes your collection of all the global ingress and egress IPs. Now lets collect your region specific IPs). If you need to deep dive this issue.
20.49.111.32/29
13.73.253.112/29
#3 Regional IP Addresses (ingress and egress):
Open this link and select your regional IP ranges from the table at https://learn.microsoft.com/en-us/azure/azure-monitor/app/ip-addresses#addresses-grouped-by-region-azure-public-cloud
Todays example will use uaenorth
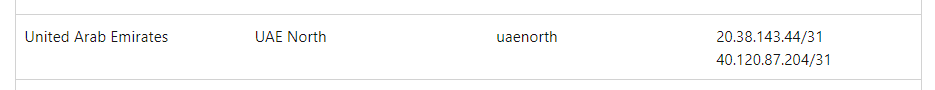
This completes your collection of your global and regional ips. Not too difficult. Just collect all the required information from 3 sources and send to your firewall team.
(The remaining steps duplicate option 1).
2. Log Analytics Workspace
a. Identify or create a destination LAW for your Application Insights
3. Application Insights
a. Sign in to the Azure portal and create your Application Insights resource
b. Select your pre-identified destination LAW > create
4. Create the Application Insights Classic Test
(The Classic Test simplifies testing instead of the Standard Test if you don’t want to include SSL features in the test)
Application Insights resource > select Availability > select Add Classic Test
(you can follow the complete process by following from here)
Option 3 - URLs that are not publicly exposed that cannot be monitored by Applications (which do not allow editing firewall rules)
For resources located inside your private virtual networks that are not allowed any external connectivity, follow my deployment scenario at this link.
very good publish, i certainly love this web site, carry on it