Go to Azure Portal > Azure Policy >
Assign initiative > select your scope = subscription or Management Group,
Select any Exclusions if required,
Basics –
Initiative definition > search for ‘ama’ >
select [Preview]: Enable Azure Monitor for VMs with Azure Monitoring Agent(AMA) > add,
Assignment name – populate a custom initiative name,
Policy enforcement > Enabled,
Next,
Advanced tab:
Resource selectors > ignore if you don’t need to filter any further,
Overrides > ignore if you don’t need to override any further,
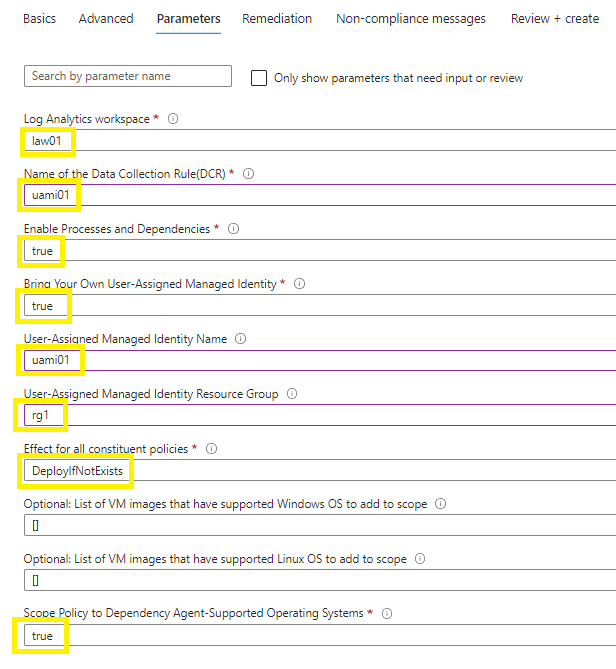
Parameters tab:
Log Analytics Workspace > add your custom workspace,
DCR > add your custom DCR,
Enable Dependencies > must be True!,
Bring your Own UAMI > True (to use your custom UAMI, else a default MI will be used),
UAMI Name,
UAMI resource group,
Effect of all policies > DeployIfNotExists,
Optional to scope to Windows VM images,
Optional to scope to Linux VM images,
Scope policy to only dependency supported OS? > True (Ive selected true to avoid errors when failing to apply AMA on hardened NVA appliances),
Next
Remediation tab:
May be skipped for now and configured later during remediation,
Non-compliance messages tab:
Optionally custom messages,
Review + create tab:
Create.
An interesting discussion is worth comment. I think that you should write more on this topic, it might not be a taboo subject but generally people are not enough to speak on such topics. To the next. Cheers
I want foregathering useful information , this post has got me even more info! .