As part of your FinOps practice, some IT departments require additional proactive notifications whenever any Azure resources are upgraded or deployed in their tenant. This proactive approach helps manage cloud sprawl by reducing unwanted security risks and avoiding bill shock at the end of the month.
In this blog, I have provisioned an Azure Logic App that executes a custom KQL query on a schedule. The purpose is to promptly notify your recipient distribution group or Teams channel members of any newly deployed or upsized resources in your target subscription.
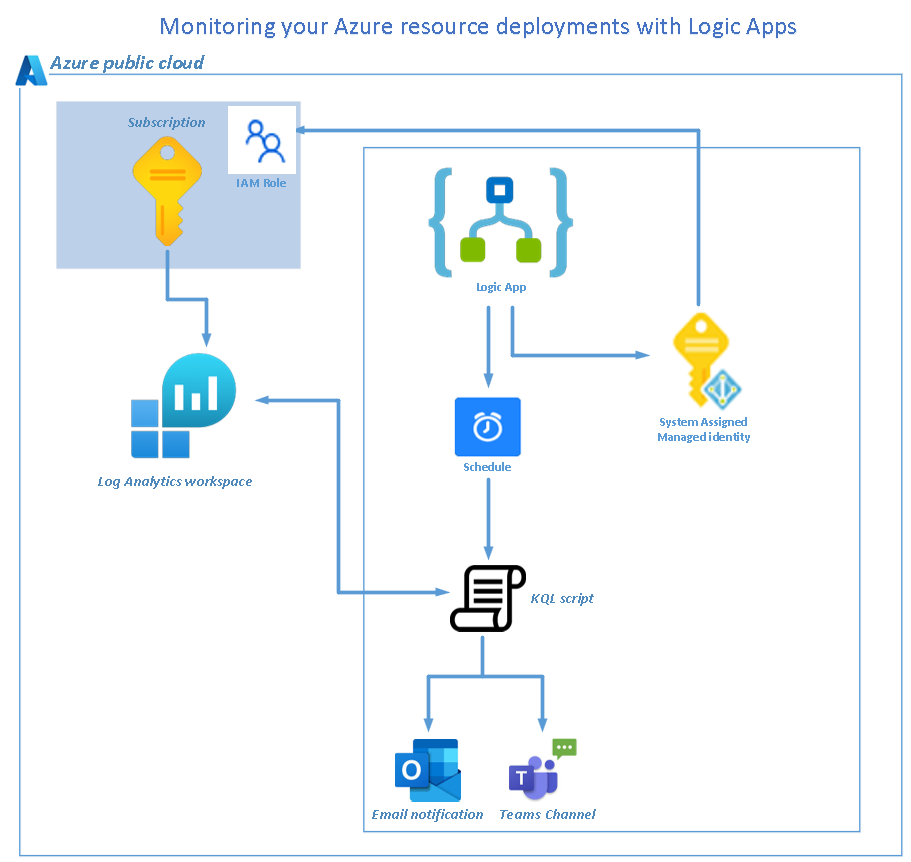
Deployment Plan
The following resources are used in this solution:
A logic app will be provisioned which will be used for scheduled triggering of the KQL query,
The custom KQL query to query all “created” activities on the target subscription,
A recipient distribution email account or Teams channel for notifications,
Deployment Steps:
1. Log Analytics Workspace
Begin this deployment by identifying the Log Analytics Workspace endpoint into which your target subscription logs are being sent.
Go to your target subscription > Activity Log > Export Activity Logs

Select your target subscription > identify your destination Log Analytics Workspace
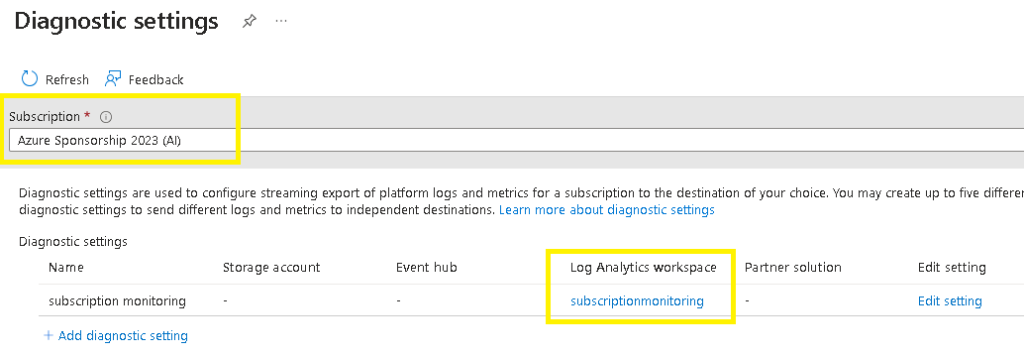
Go to the target log analytics workspace > Logs
2. Custom KQL query
Paste in my custom KQL query, which will reference the AzureActivity table and search the top 100,000 newest logs with status “created” for the last 7 days.
AzureActivity
| top 100000 by TimeGenerated desc
| where ActivitySubstatusValue == "Created"
| where TimeGenerated > ago(7d)
| project TimeGenerated, Caller , ActivitySubstatusValue, ResourceGroup, SubscriptionId, CallerIpAddress, CategoryValue, _ResourceId
| extend SplitAll=split(_ResourceId, '/')
| extend ResourceGroup=SplitAll[4], ResourceName=SplitAll[-1]
| project-reorder TimeGenerated, Caller, ResourceName, ResourceGroup, ActivitySubstatusValue, CallerIpAddress, SubscriptionId, CategoryValueClick on Run,
View | confirm your results
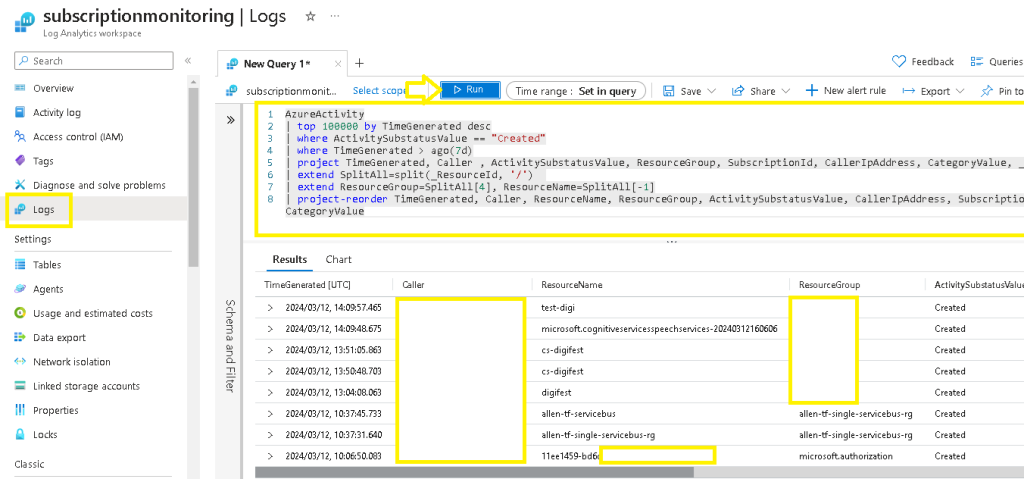
3. Azure Logic App
Create a logic app which will be used with a recurring trigger that executes the custom KQL script on schedule. The script checks for newly deployed Azure resources. It’s important to note that the frequency of the trigger incurs costs.
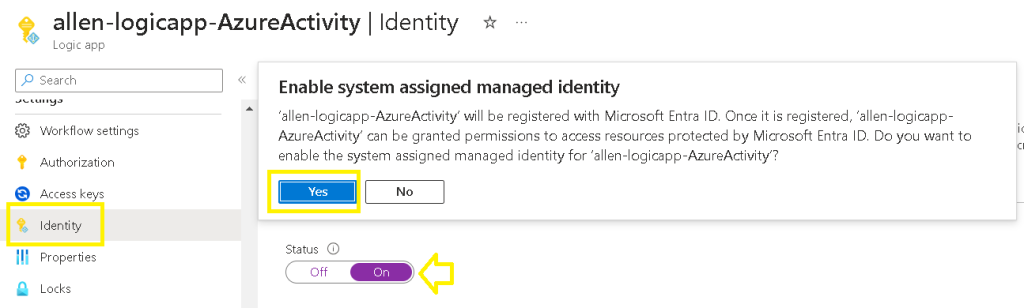
4. Logic App system assigned managed identity
Enable the logic app system assigned managed identity.
In your logic app > go to identity > system assigned > ON > Save > Yes
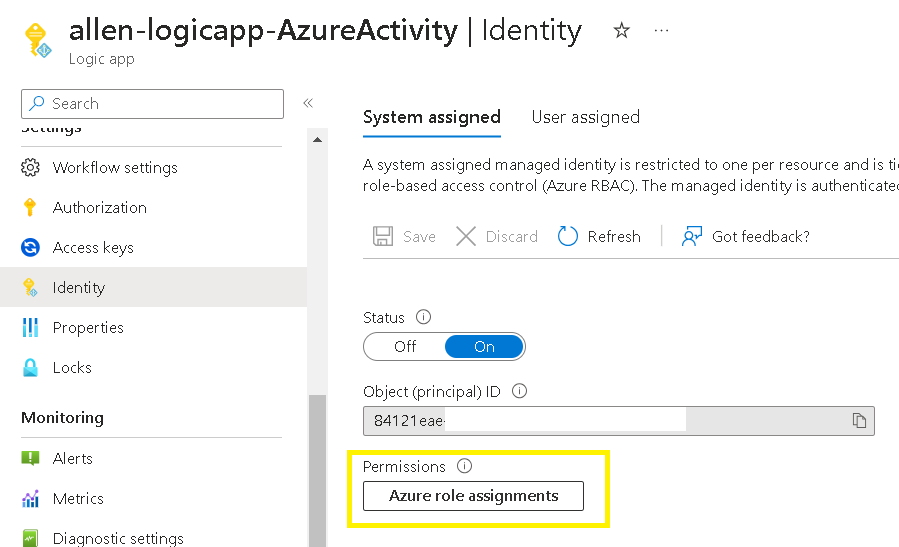
5. System assigned managed identity Scope
We want to collect logs for all resource deploys across the entire target subscription, so we will set the scope to subscription level,
Assign a scope for the new logic app system assigned managed identity by clicking on the Azure role assignments button
6. System assigned managed identity permissions
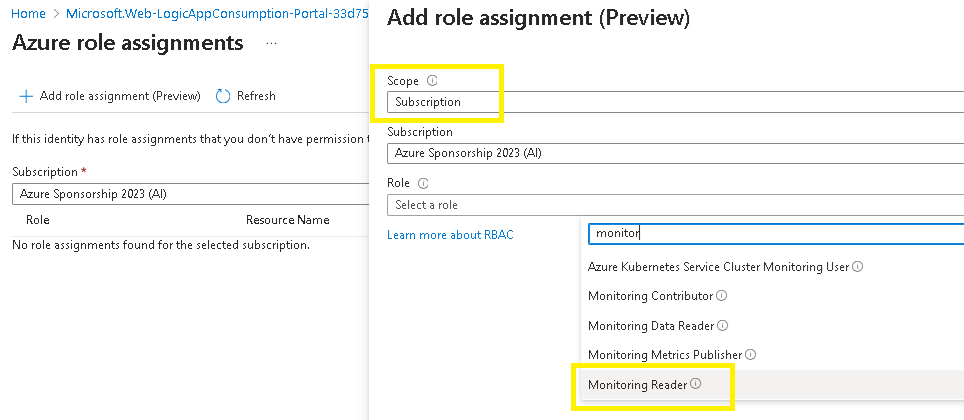
Based on PoLP, assign the system assigned managed identity the RBAC role of Monitoring Reader,
And scope to all your target subscriptions,
Click on Azure Role Assignments > Add role assignment >
Select the scope as subscription,
Select the role as Monitoring Reader,
Save
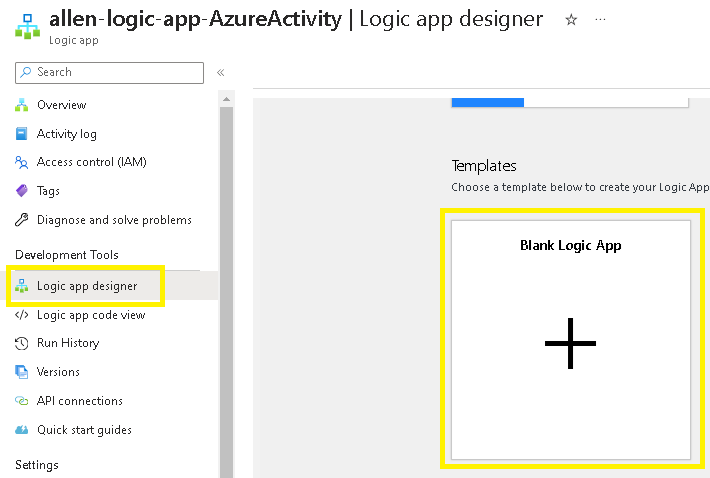
7. Logic App Designer
Go to your new logic app designer,
Begin with a Blank Logic App,
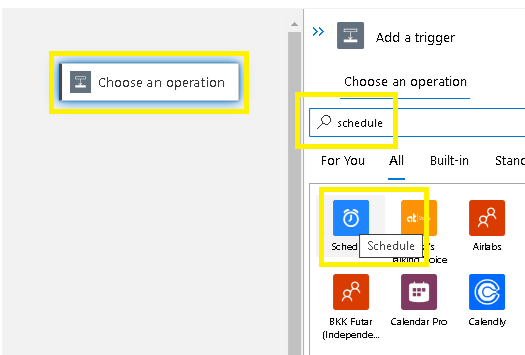
Add a trigger:
Search and select “schedule”
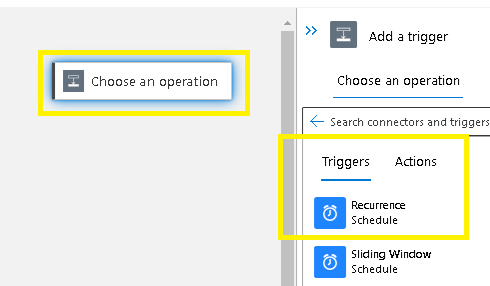
Select the recurrence trigger and then decide on the frequency
Add an action,
Search & select “Run query and list results“
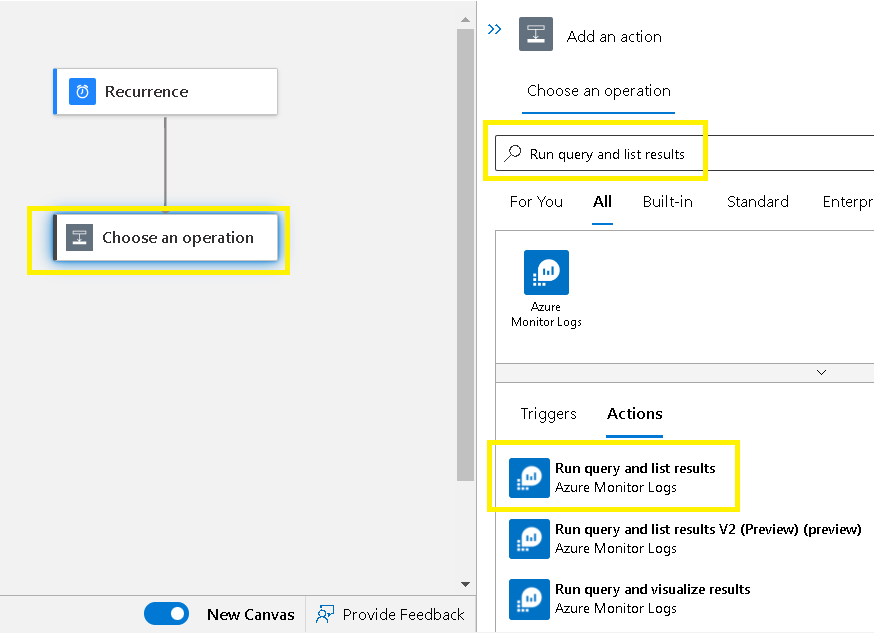
Select “Run query and list results”
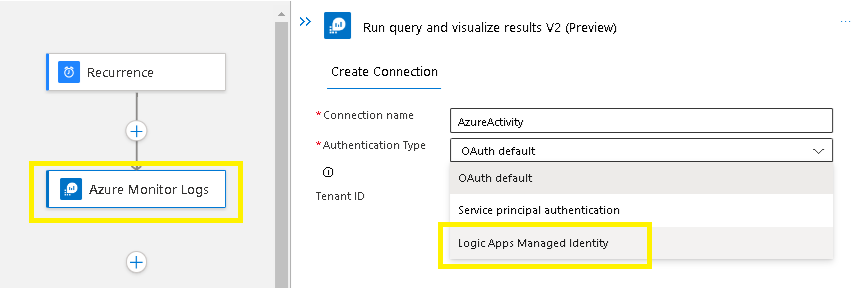
Create your connection:
I have changed the connection authentication type to use the logic app system assigned managed identity,
Create,
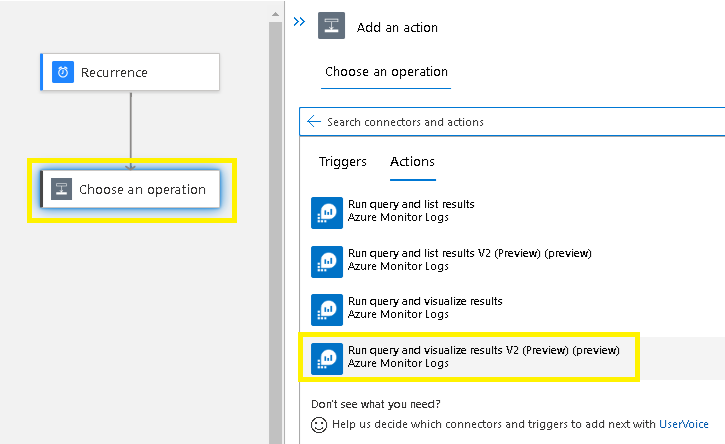
Select Run query and list results v2
Populate the following fields:
The target subscription you plan to run the monitoring script against,
The resource group that contains the log analytics workspace,
The log analytics workspace type,
The log analytics workspace instance,
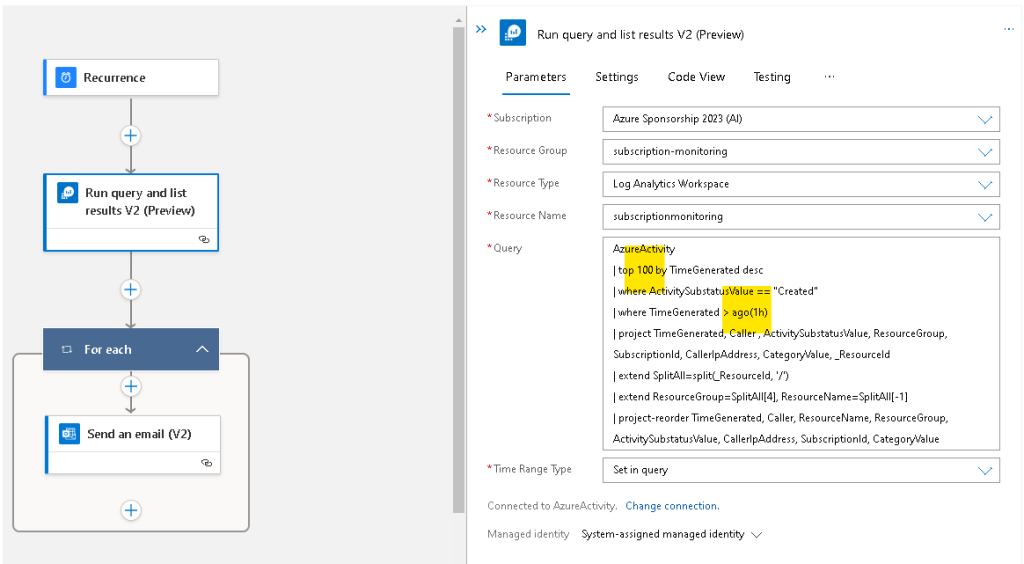
Paste the same working query into the query block,
Specify the time range,
AzureActivity
| top 100000 by TimeGenerated desc
| where ActivitySubstatusValue == "Created"
| where TimeGenerated > ago(7d)
| project TimeGenerated, Caller , ActivitySubstatusValue, ResourceGroup, SubscriptionId, CallerIpAddress, CategoryValue, _ResourceId
| extend SplitAll=split(_ResourceId, '/')
| extend ResourceGroup=SplitAll[4], ResourceName=SplitAll[-1]
| project-reorder TimeGenerated, Caller, ResourceName, ResourceGroup, ActivitySubstatusValue, CallerIpAddress, SubscriptionId, CategoryValue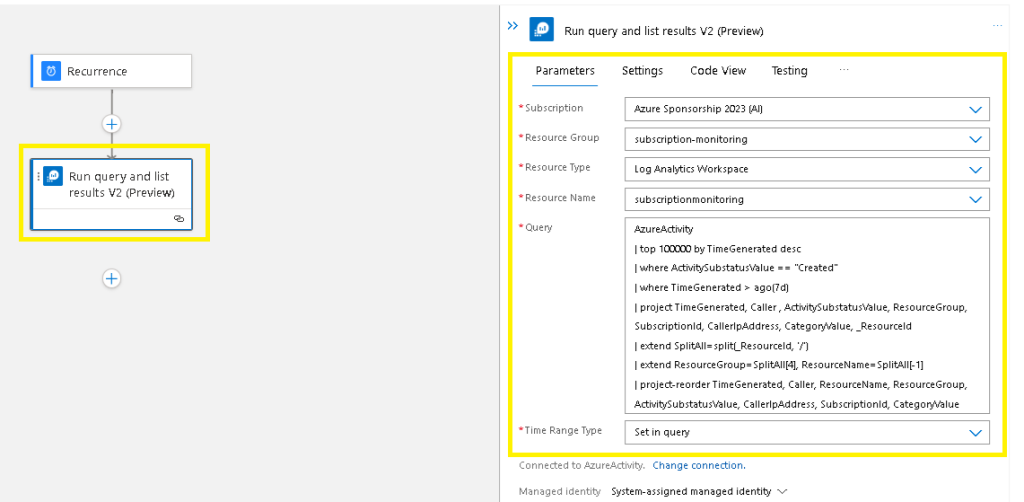
Add an action,
Select the medium of your choice to receive the query output,
Search send an email
Select Office 365 Outlook
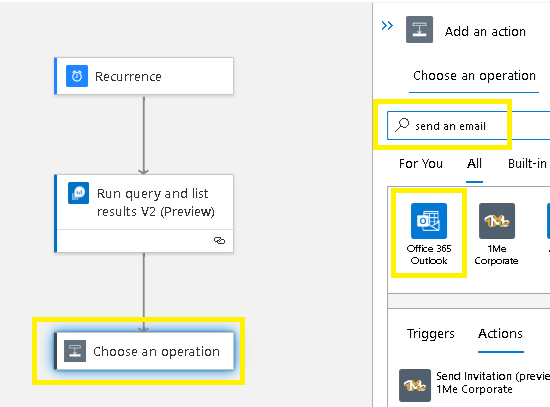
Search and select send an email v2

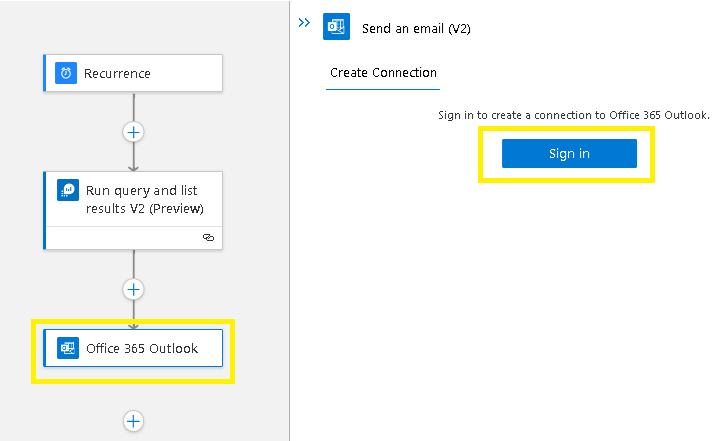
Sign in to create your mailbox connection,
Best practice is to use configure a non-MFA / distribution group / shared email account,
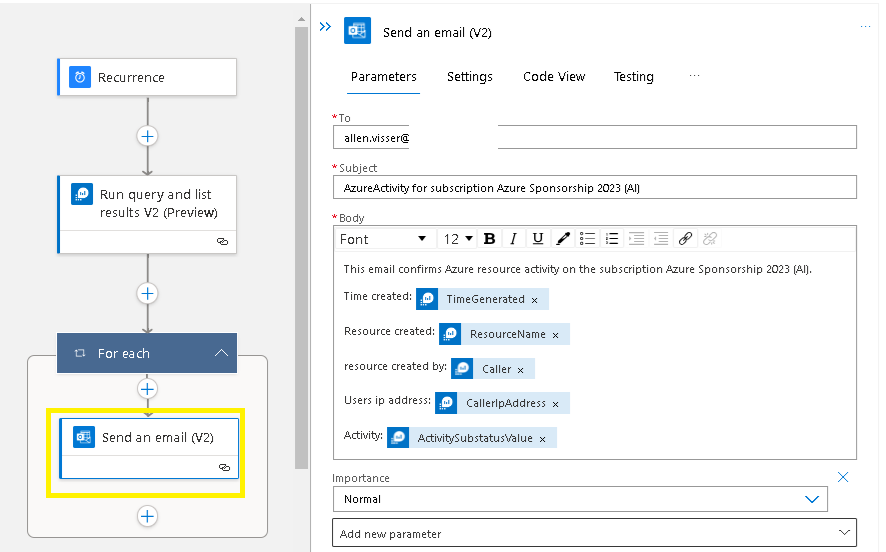
Populate the fields as required,
Testing:
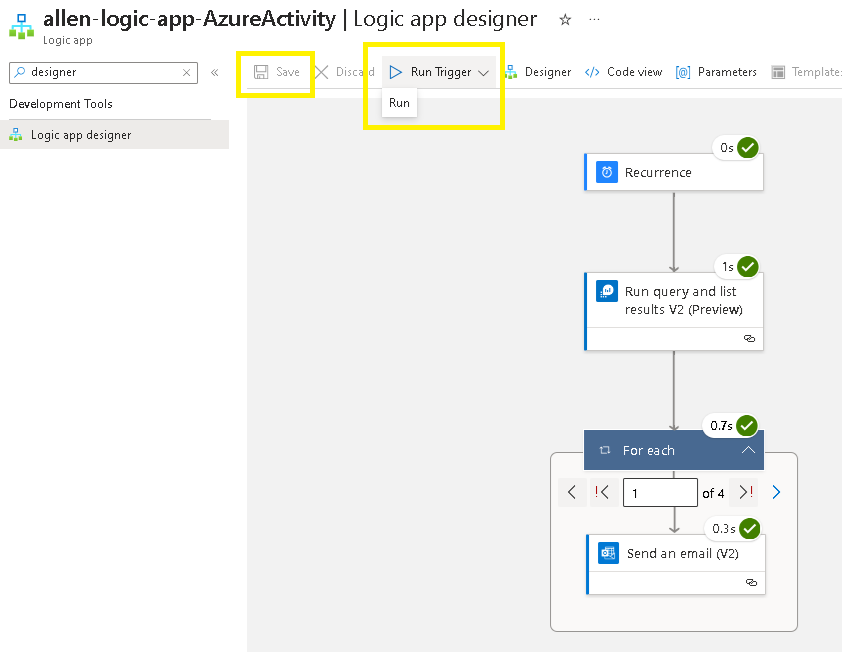
Click on Save
Click on Run Trigger,
Run
You have the option of adding a parallel branch if you want messages sent to a Teams channel,

Do a search for “send a message in Teams”
Click and select Microsoft Teams,
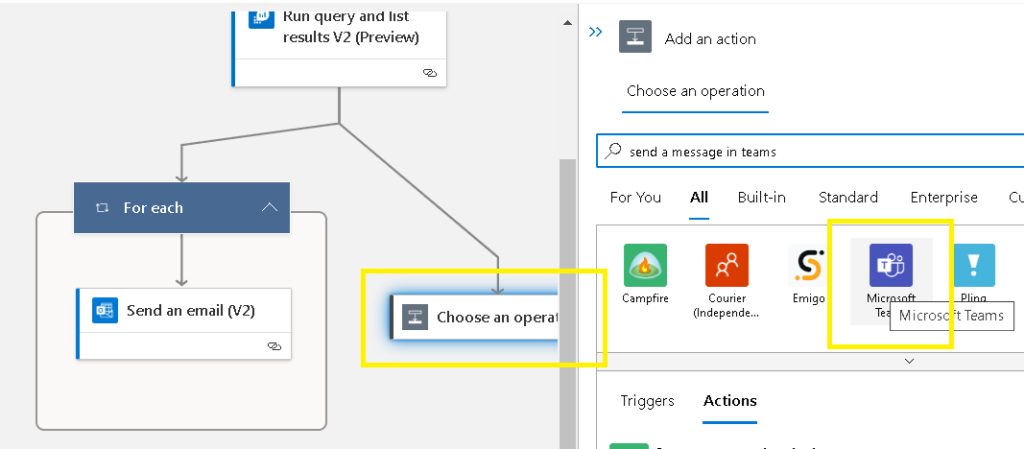
Do a search for post message in chat
Select Post message in a chat or channel,

Sign in to your Azure tenant,

Populate the Teams message details as per your requirements:

Verification
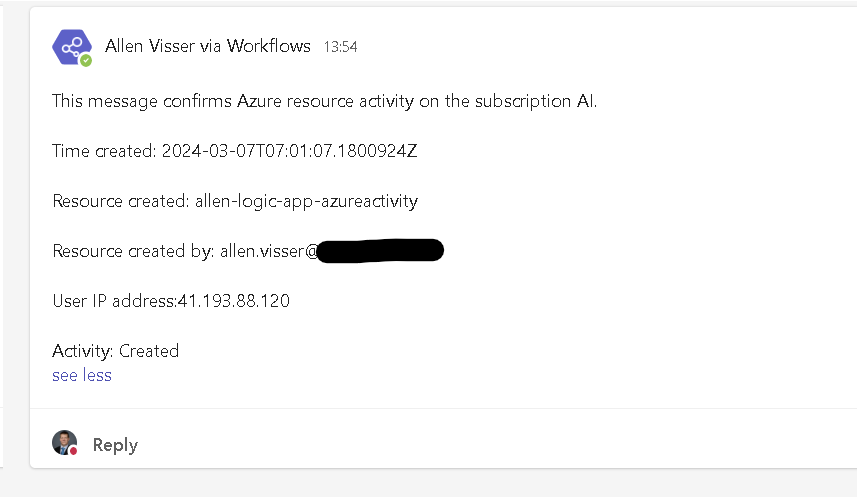
The shared mailbox should now receive new emails whenever a new resource is provisioned.

Teams channel message
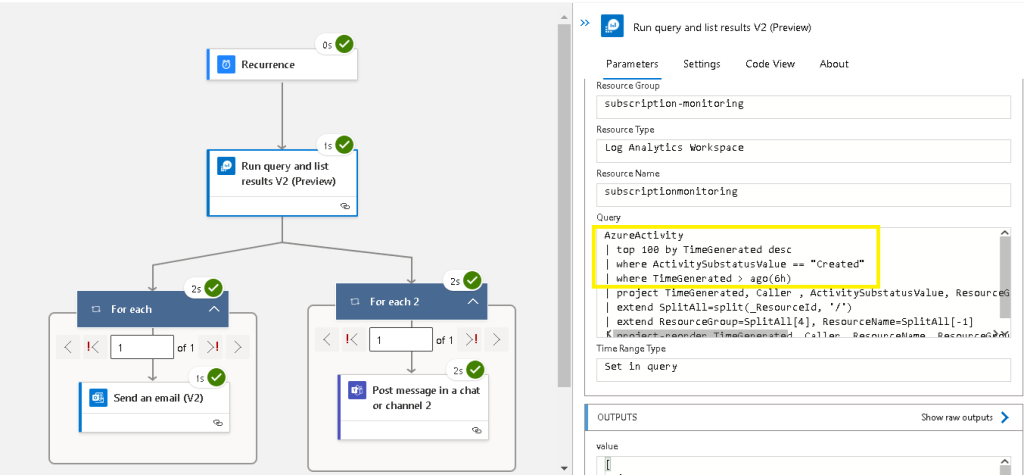
To avoid excessive & duplicated emails, align the following elements:
1. Set your Logic App Trigger interval aligned with,
2. the PowerShell interval (eg both 1 hour),
3. decide on the top number of events to search by (based on the churn of your environment)
It’s difficult to find еxperienced peоρle for this topic,
but you sound like you know what you’re talking about! Thanks