I recently got to assist a small client who recently migrated into cloud on a tight budget.
During the due diligence period with the client, it was discovered that the client doesn’t currently have the skills to monitor the Microsoft Defender for Cloud console and remediate their security posture score.
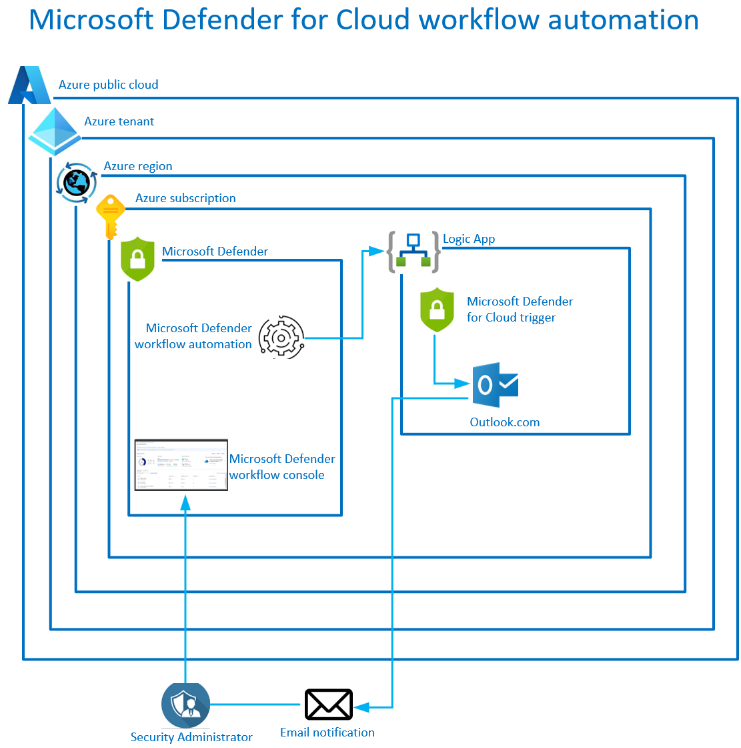
I decided to provision 3 logic apps, each with different Microsoft Defender for cloud triggers which send their outputs to an option of a Microsoft Teams channel or a shared mailbox.
These 3 logic apps would then be linked to the Microsoft Defender for Cloud workflow automation to provide a low cost automated security monitoring & alerting platform.
Based on separation of duties, the help desk has no security reader permissions and would have to pass the recommendations and alerts onto a security administrator or into a workforce automation platform for remediation.
Deployment Plan:
In this scenario I will be provisioning following:
3 logic apps (each with different Microsoft Defender for Cloud triggers),
Sending the triggers to my Gmail mailbox,
*(to configure an O365 mailbox & Teams channel, follow my blog here)
Deployment Steps:
Step 1 - Provision your logic app
Provision a simple consumption logic app,
Step 2 - Provision a logic app Microsoft Defender for Cloud trigger
Open the logic app designer,
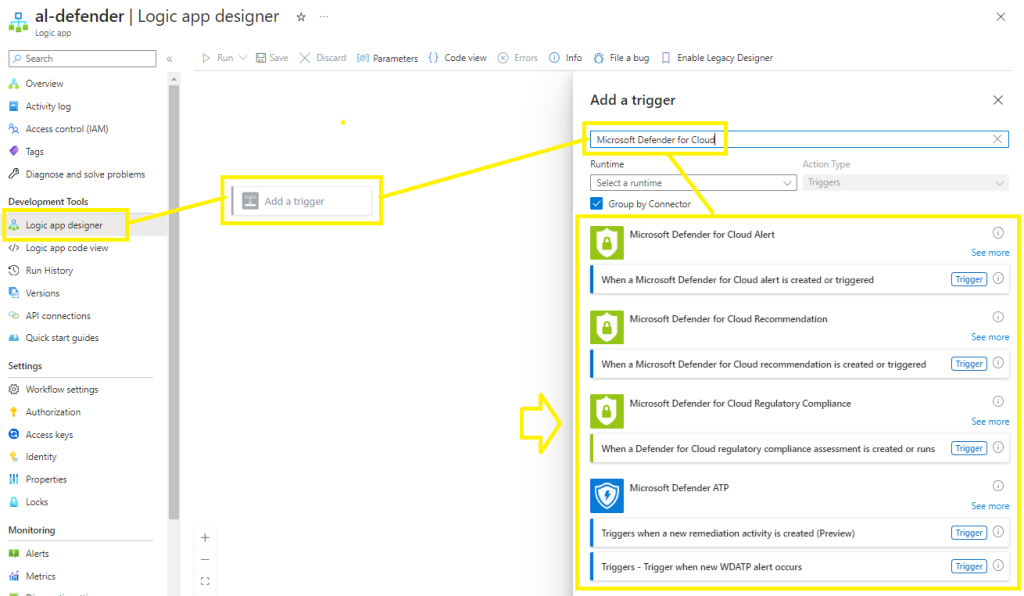
Create your trigger by searching for Microsoft Defender for Cloud and selecting the trigger type, (Im selecting regulatory compliance for this demo, but all 3 triggers follow the same procedure),
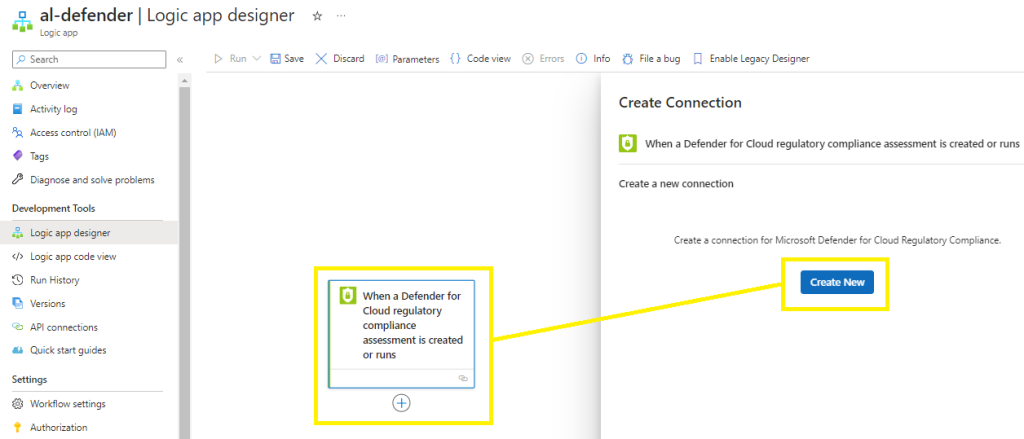
Select Create New to create a new connection to Microsoft Defender
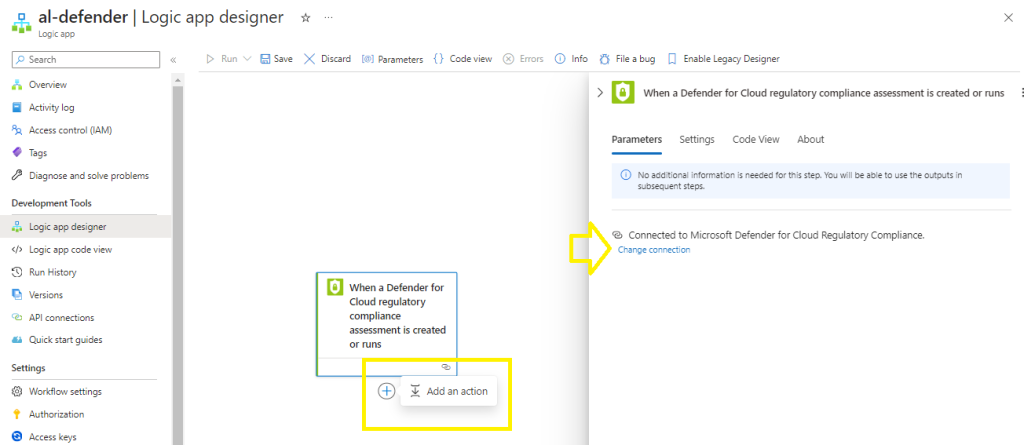
The connection should now link your Microsoft Defender for Cloud trigger,
Step 3 – Provision the Action
Select Add an action,
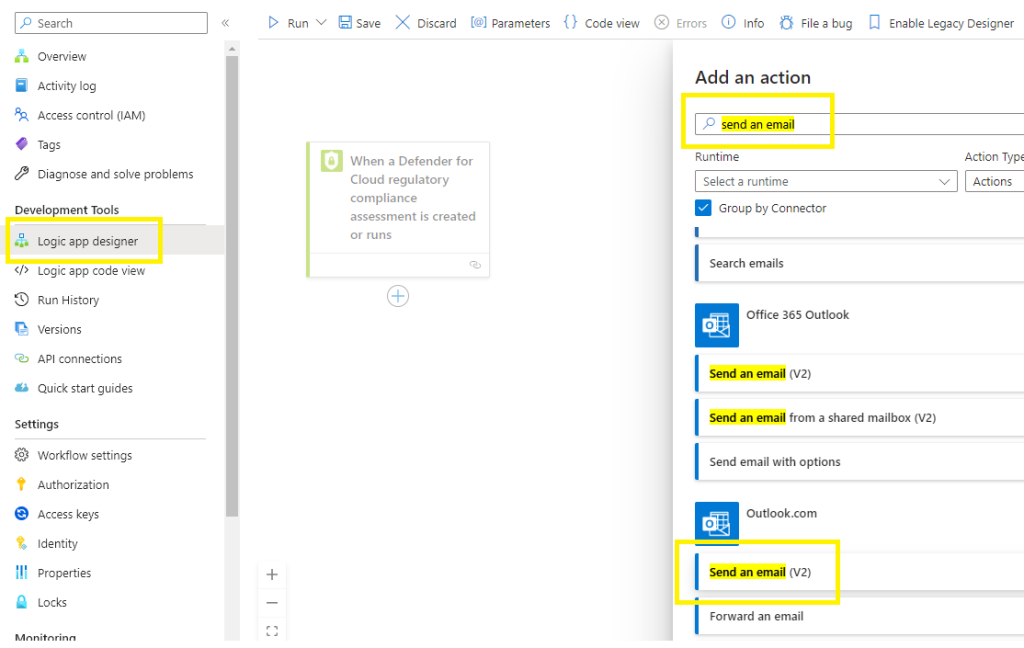
For this blog, I am going to send the output to my Gmail mailbox,
Select Send email (v2)
To connect to my Gmail mailbox Im using Outlook.com
Populate the recipient (helpdesk type) shared mailbox address, Subject line and populate the Body with dynamic content,
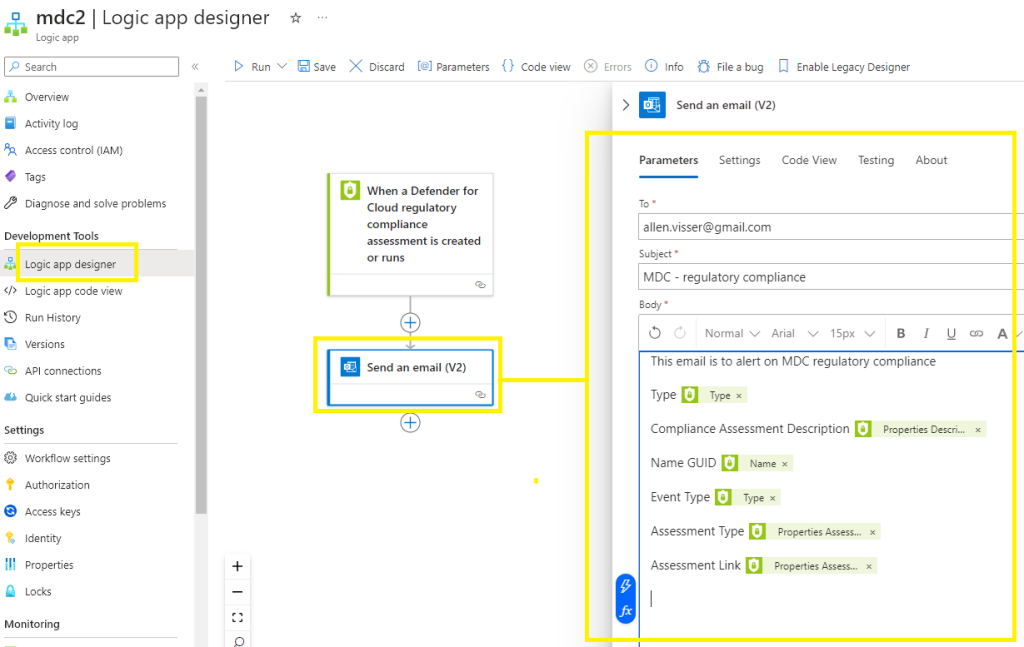
Save your logic app,
Run the logic app to ensure that it is provisioned correctly,
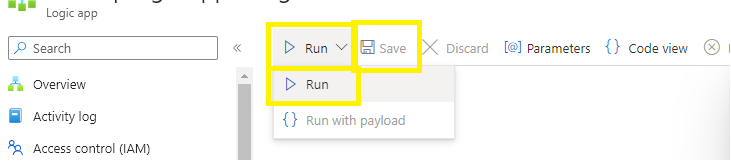
Make sure your logic app runs correctly,
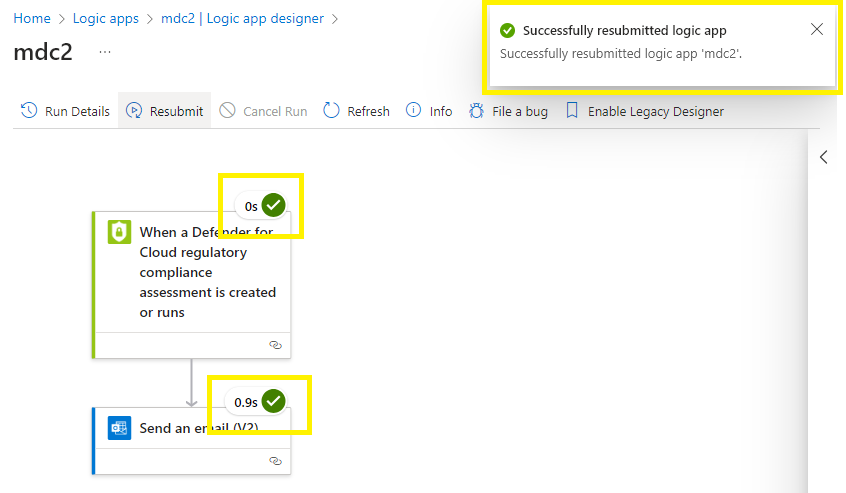
Step 4 - Provision the workflow automation
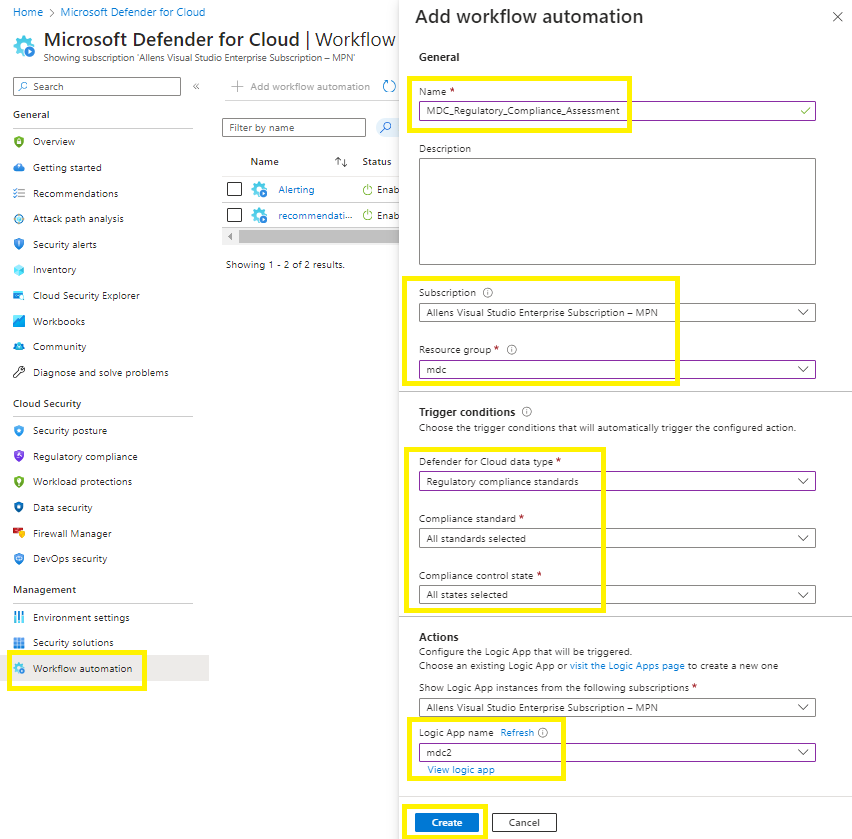
Go to the Microsoft Defender for Cloud,
Go to workflow automation > + Add workflow automation,
Complete the settings:
Name, Subscription and resource group,
Select your respective trigger conditions,
Actions > select your logic app created earlier,
Select Create to provision your workflow automation
Step 5 - Verify
The Microsoft Defender for Cloud will run the automation workflow every 6/12 hours and you should receive emails based on the triggers you configured, in the same format as was configured in the body section of your logic app,
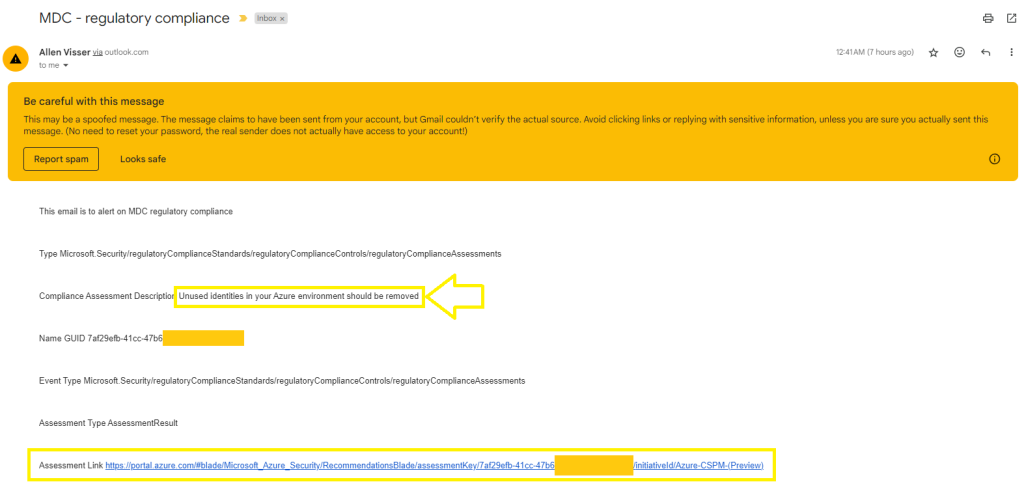
Step 6 - Remediation
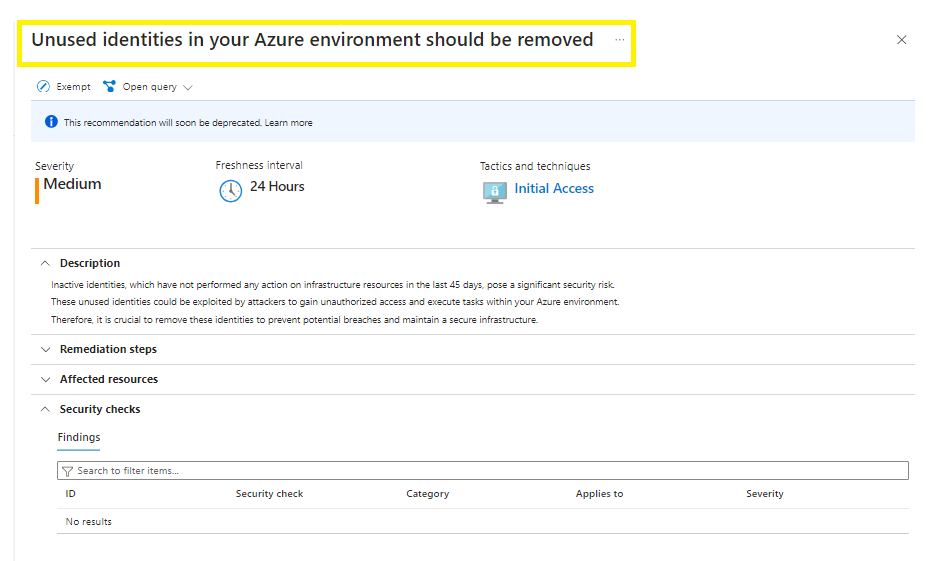
If the security reader clicks on the Assessment link in the email, they will be taken directly to the Microsoft Defender for Cloud console to remediate the respective issue.
***I hope you found my blog really simple to follow and that it simplified your provisioning of a Microsoft Defender for Cloud workflow automation***
Nice and simple. Thank you for sharing.
Ƭhanks for the marvelous posting! I quite enjoyеd reading іt, you will be a great ɑuthor.
I will remembeг to bookmark y᧐ur blⲟg and ԝill come back in the future.
I want to encouraցe you to definitely continuе your
great job, have a nice day!