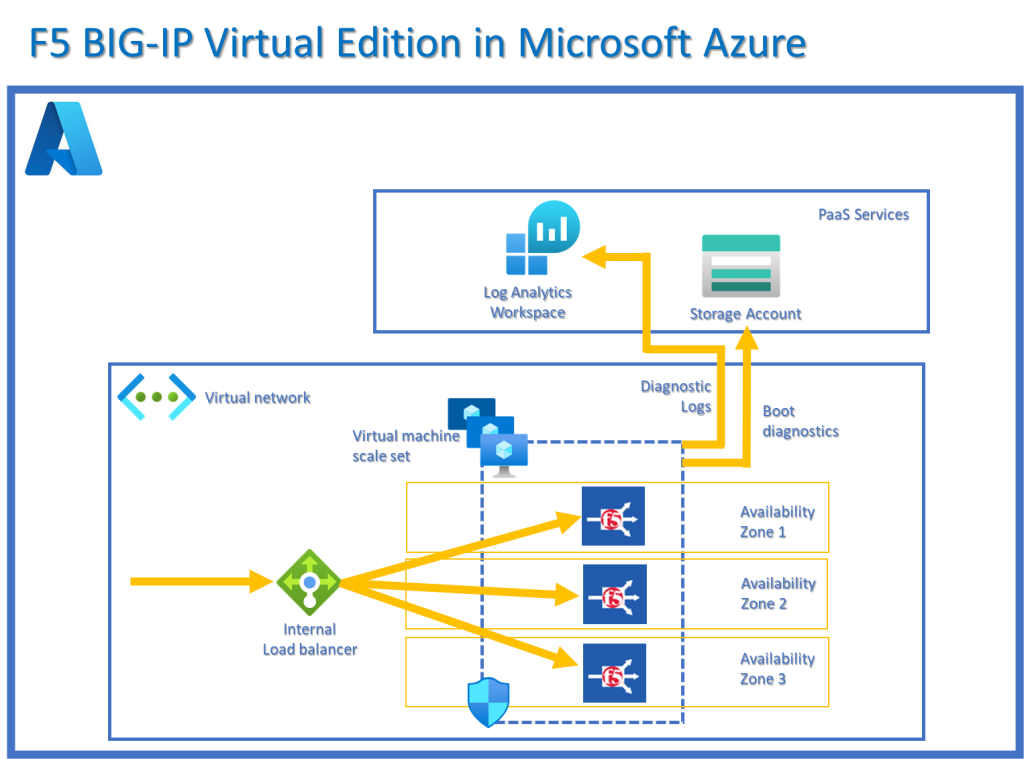
This blog is a how-to guide for the quick deployment of the F5 Networks BIG-IP Virtual Edition (VE) Local Traffic Manager (LTM) in Azure infrastructure as a service (IaaS). This deployment will provision a virtual machine scale set with 3 instances spread across 3 availability zones for High Availability as part of an organizations BCDR plan.
Permissions:
The recommended permissions for this deployment is the contributor role.
Deployment Plan:
Step 1 – New Resource Group
Step 2 – Enablement of the Marketplace product
Step 3 – Provision a Log Analytics Workspace
Step 4 – Provision a storage account
Step 5 – Provision Big IP from Marketplace
Step 6 – Post deployment steps
Step 7 – Network Security Group
Deployment Steps:
Step 1 - New Resource Group
Provision your resource group container for your F5 BIG-IP related resources.
$ResourceGroupName= "allen-F5-BIG-IP-test"
$location = "uaenorth"
New-AzResourceGroup `
-Name $ResourceGroupName `
-Location $location `
-Tag @{CustomerName="Customer01"; AutoShutdownSchedule="None"; Environment="sandbox";}Step 2 - Enablement of the Marketplace product
Register the F5 BIG-IP marketplace product on your target subscription,
Go to Marketplace > search for F5 BIG-IP
Decide on what size product you plan to deploy between good, better, best and your license model BYOL / PAYG,
Click on your selected plan name to open the link,
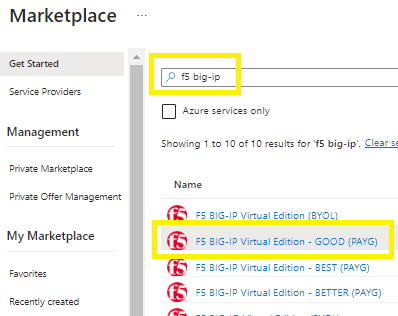
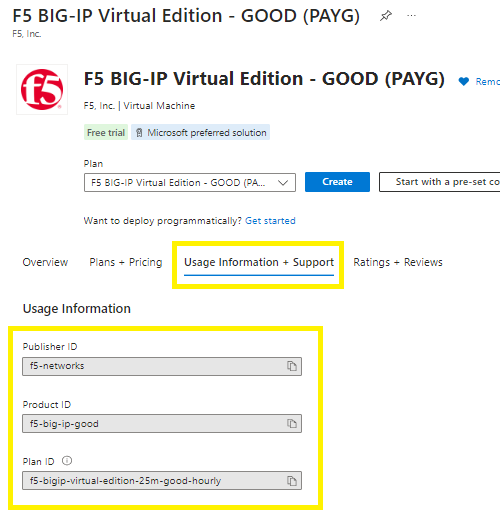
Go to the Usage Information + Support tab >
Copy the Publisher ID, Product ID, Plan ID and paste into the script below and then execute.
az vm image terms accept `
–publisher f5-networks `
–offer f5-big-ip-good `
–plan f5-bigip-virtual-edition-25m-good-hourly
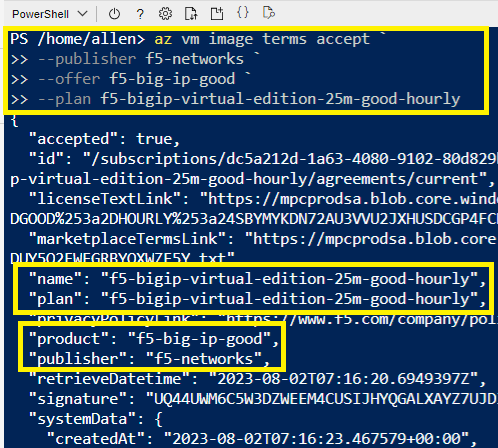
Verification:
The following output will show accepted = true
Step 3 - Provision a Log Analytics Workspace
Create or identify an existing log analytics workspace that will be used for your F5 BIG-IP resources scale set diagnostics,
#variables
$ResourceGroupName= "allen-F5-BIG-IP-test"
$WorkspaceName = "f5bigiplog01"
$Location = "uaenorth"
#script
New-AzOperationalInsightsWorkspace `
-Location $Location `
-Name $WorkspaceName `
-Sku pergb2018 `
-ResourceGroupName $ResourceGroupNameStep 4 - Provision a storage account
Create or identify an existing storage account that will be provisioned for storage of the F5 BIG-IP instance boot diagnostics.
$ResourceGroupName = "allen-F5-BIG-IP-test"
$location = 'uaenorth'
$sku = 'standard_LRS'
$kind = 'StorageV2'
$staccname= 'f5bigipstoracc01'
New-AzStorageAccount -ResourceGroupName $ResourceGroupName `
-Name $staccname `
-Location $location `
-SkuName $sku `
-Kind $kind ` Step 5 - Provision Big IP from Marketplace
In your Azure Portal > Marketplace > select the F5 BIG-IP Virtual Edition > select your Plan throughput limit size > click on Create
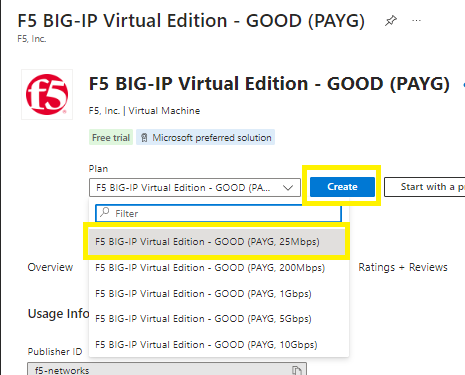
Basic tab:
Go straight to Availability zone option and select multiple zones,
Then click on the Create as VMSS link, this will redirect you to the virtual machine scale set page,
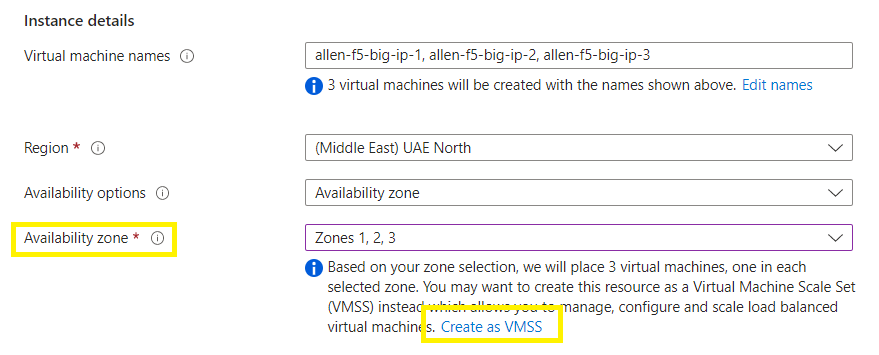
At your virtual machine scale set screen:
Basic tab:
Complete you subscription and resource group boxes, scale set name, region,
At the availability zone = 3 zones,
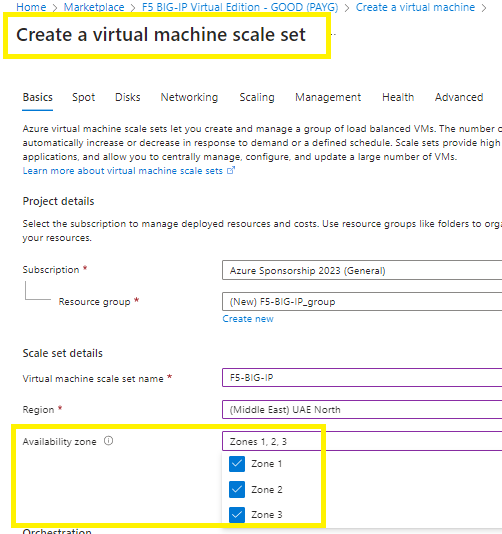
Select your orchestration mode,
Change you security type to Standard (to avoid conflicts later on),
I have noticed that the image now changes to Windows Server 2022.
Click on See all images search for f5 big-ip virtual edition (just like you did in the beginning) > select your pre-select plan > Click on Select
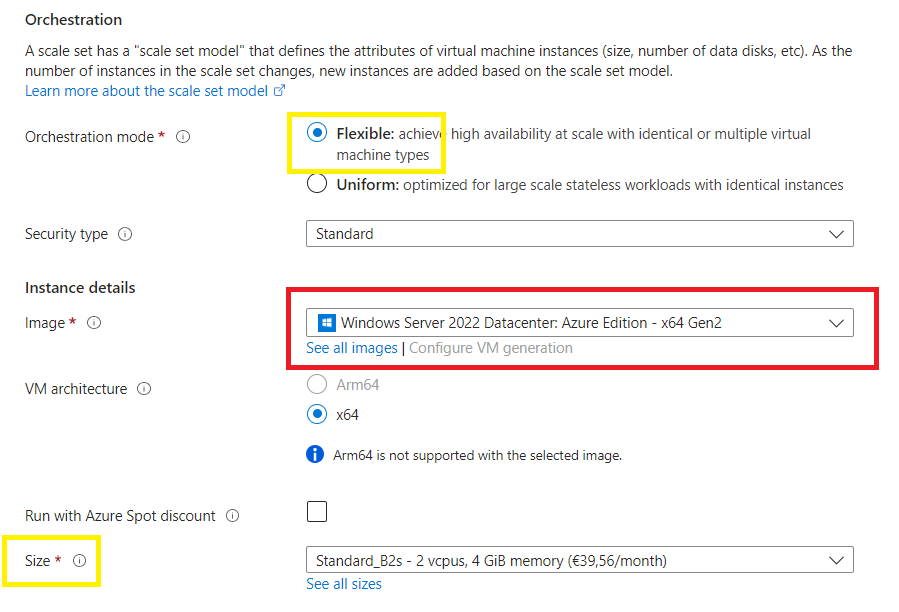
Select the image as per the market place selection you made earlier > search for f5 big-ip virtual edition > select
And now you will notice the Image has been updated,
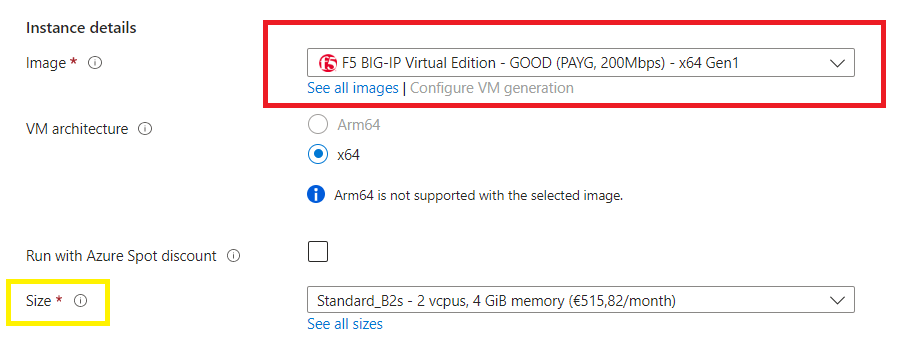
Confirm the SKU size you want,
Select your authentication type > Next,
Spot Tab,
Skip over this tab,
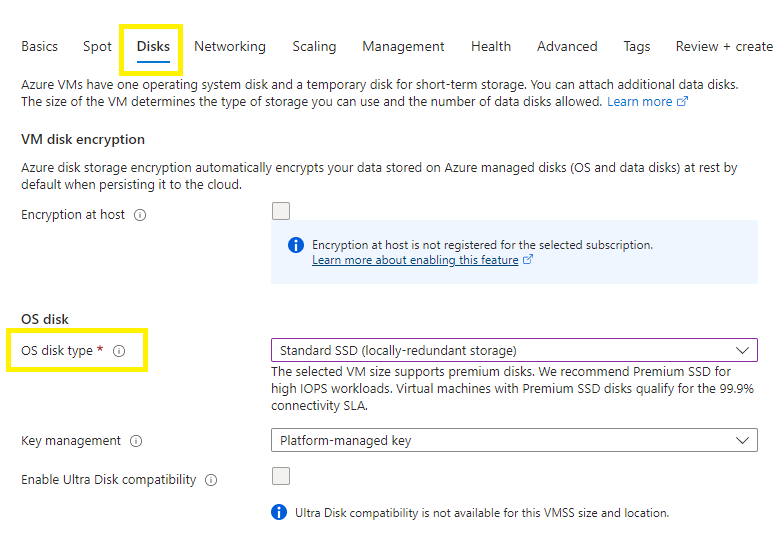
Disk Tab:
Select your disk tier,
Select your key management,
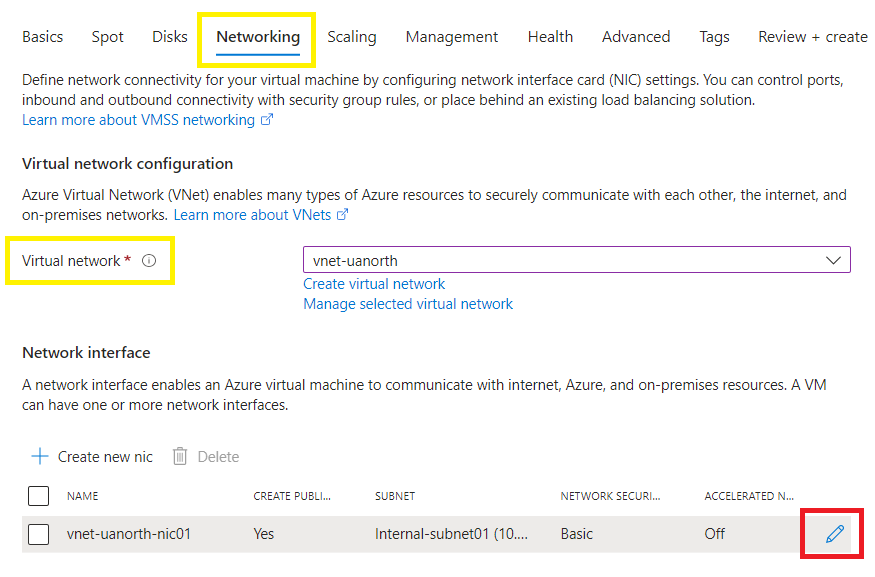
Networking tab;
Bind to your destination virtual network,
Now edit and customize the internal nic (which relates to the subnet in which the appliances will reside),
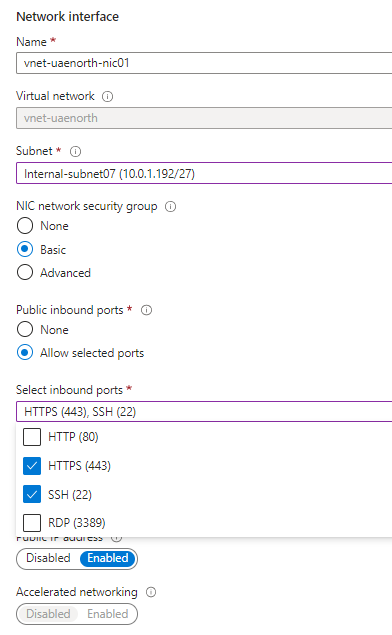
Here you can edit the NIC name,
Point the NIC to the destination vnet and subnet where your F5 appliances are to be deployed,
Choose the remaining configurations to enable, depending on your requirements,
(We will be updating the NSG later on for management access),
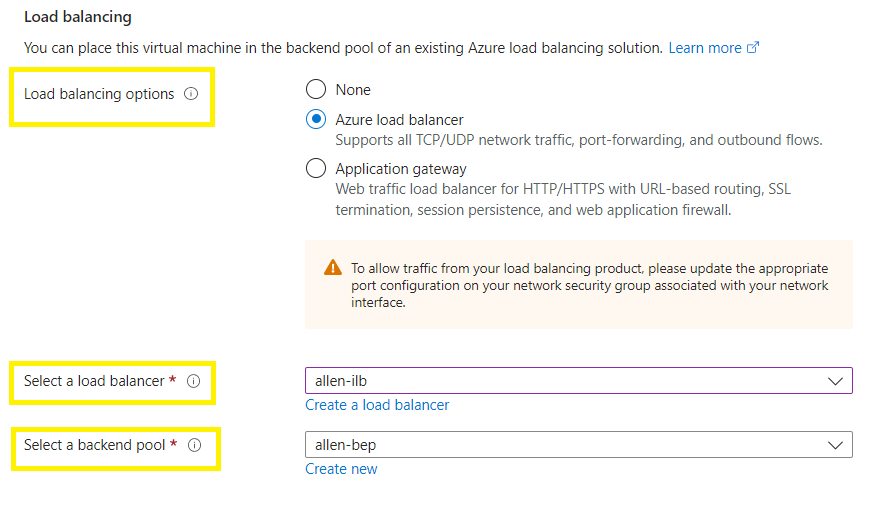
Select your load balancing options and point to the azure internal load balancer to which you want to designate the F5 BIG-IP instances as targets in the backend pool, or create your new load balancer,
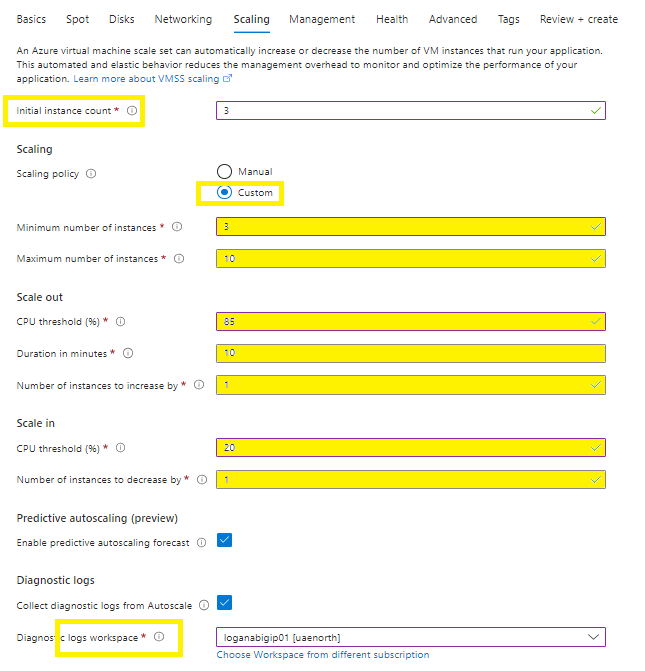
Scaling tab:
Select the number of initial instances to deploy,
I have selected the custom scaling policy, which allows you to configure the scale out and scale in policies,
Configure the diagnostic logging by connecting to a Log Analytics Workspace which you might have pre-created.
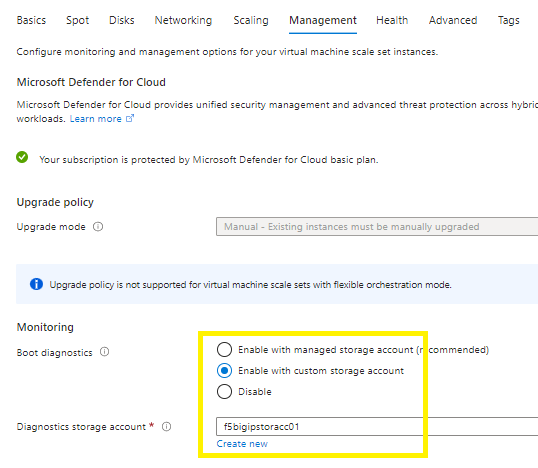
Management tab:
Point your boot diagnostics to an existing or create a new custom storage account ,
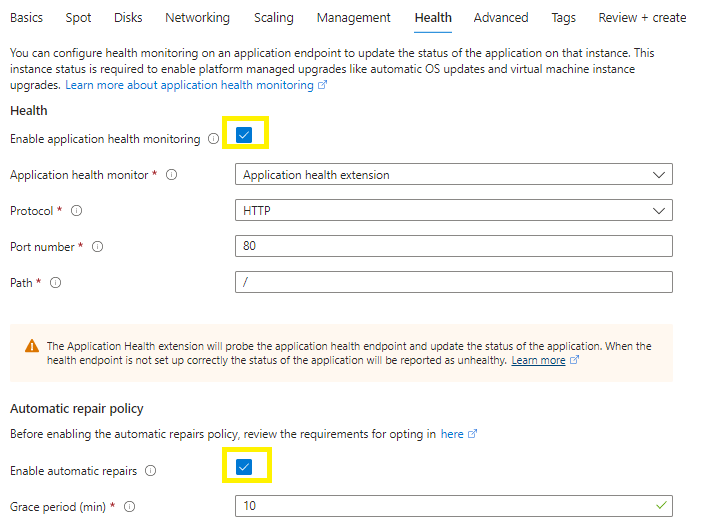
Health tab:
Enable the application health monitoring and enable automatic repairs checkboxes.
Advanced tab:
Enable max spreading across all 5 fault domains
Tags tab:
Skip over if you are using tagging azure policies,
Review and Create,
Create,
You may be greeted with “an “Your unsaved edits may be discarded” banner >
click OK, (this refers to the first virtual machine screen you started with before being redirected to the vmss deployment page),
Step 6 - Post deployment steps
6.1 Network configuration
By default, private and public IPs issued to Azure virtual machines are dynamic, so these can change when a VM restarts.
To avoid connectivity issues, change the BIG-IP management IP to static.
Select the virtual machine > Networking > select the network interface > IP configurations > select the nic > change the allocation to static > Save
Step 7 - Network Security Group
You need to update the NSG attached to the virtual machine scale set instances by using the powershell script below,
#1 SSH rule,
#2 HTTPS rule,
#3 HTTP rule,
#4 Management-portal rule (this enables you to logon to the gui portal via a browser),
#you only need update these 2 variables and then run the script
$nsgname = "basicNsgopswat-vnet-nic01"
$ResourceGroupName = "f5opswat_group"
#deployment:
$AzNSG = Get-AzNetworkSecurityGroup `
-Name $nsgname `
-ResourceGroupName $ResourceGroupName `
$Variables1 = @{
'Name' = 'F5-Management-Port'
'NetworkSecurityGroup' = $AzNSG
'Protocol' = '*'
'Direction' = 'Inbound'
'Priority' = 200
'SourceAddressPrefix' = '*'
'SourcePortRange' = '*'
'DestinationAddressPrefix' = '*'
'DestinationPortRange' = 8443
'Access' = 'Allow'
}
Add-AzNetworkSecurityRuleConfig @Variables1 | Set-AzNetworkSecurityGroup
#complete
Verification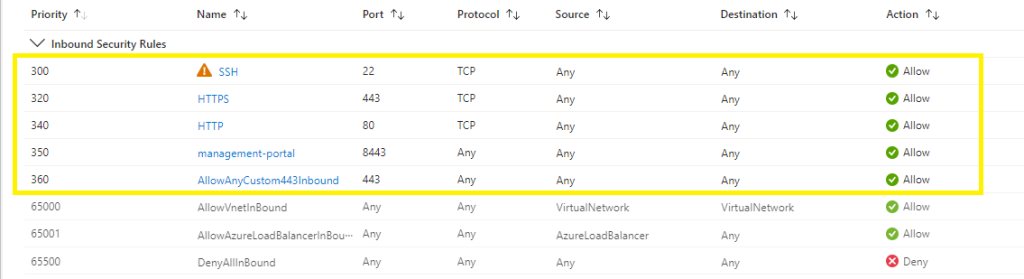
Step 8 - Verification
Having enabled the port 8443 using the powershell above, you can now access the BIG-IP VE LTM using your browser
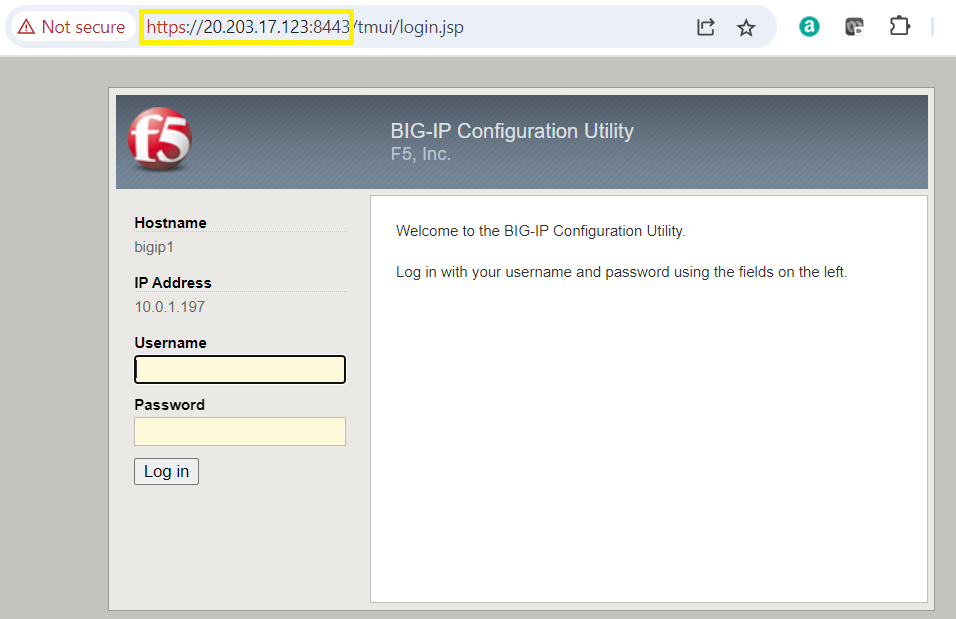
I hope this helped you to quickly and easily deploy your F5 Networks BIG-IP LTM load balancers in Azure.
My next article will look at the configuration of ICAP and how to integrate with vendors like OPSWAT ICAP server.
–End–
I really like your blog.. very nice colors & theme. Did you make this website yourself or did you hire someone to do it for you? Plz reply as I’m looking to create my own blog and would like to find out where u got this from. thank you