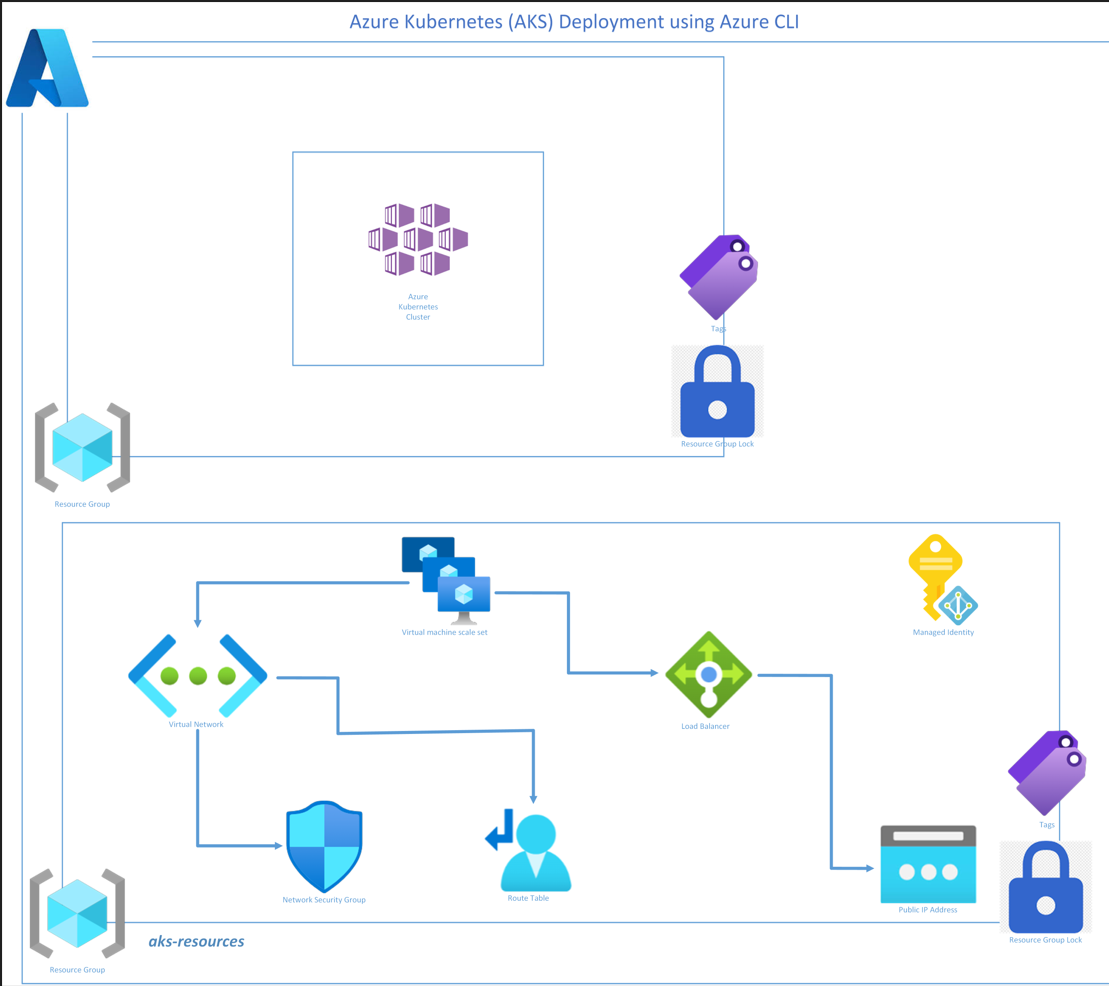
The aim of my blog is to provide a level 100 walkthru on how to quickly and easily deploy an Azure Kubernetes Service (AKS) using Cloud Shell, in 3 easy steps. The cloud shell offers you the option of applying tagging and resource group locks as well as a customzing the k8s node resource group… Continue reading Deploying (AKS) using Cloud Shell
Author: allen.visser
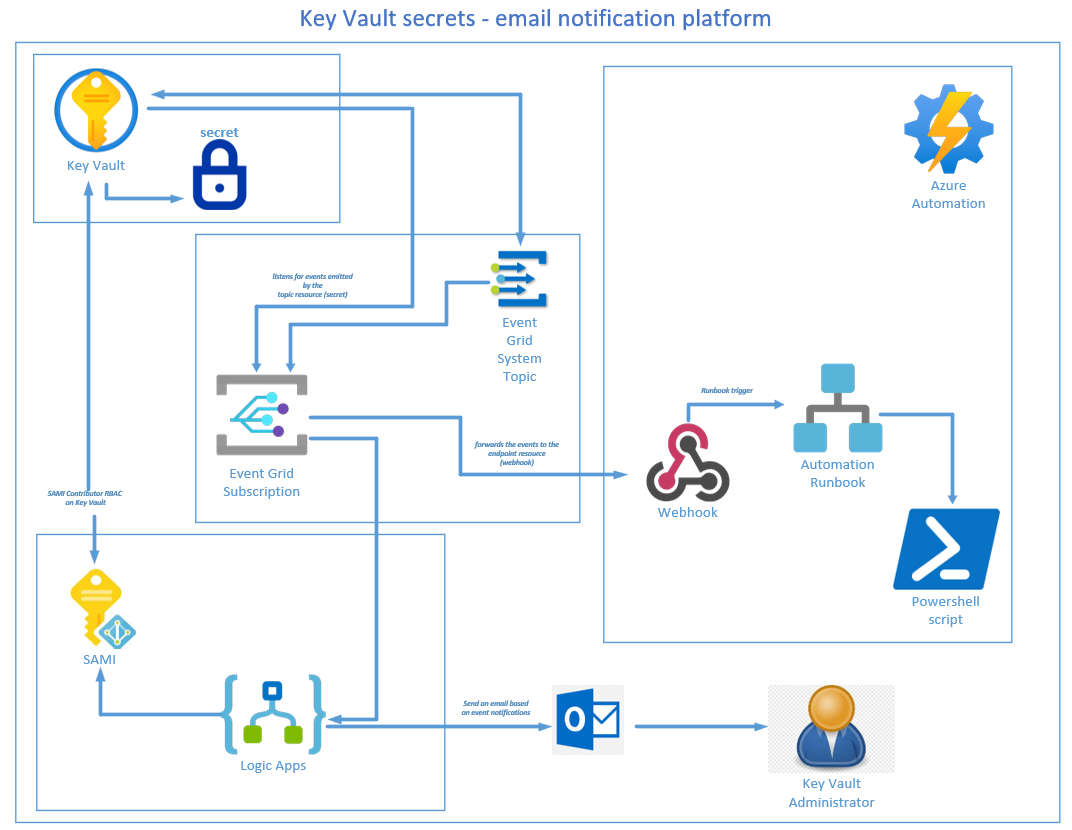
Key Vault secrets – email notification platform
The aim of this blog is to easily configure a proactive email notification platform to notify you at least 30 days before your key vault based secrets expire, or if any other key vault secrets statuses changes. Key vault secrets consists of all keys, certificates, and secrets,Status changes are defined as:About to expire < 30… Continue reading Key Vault secrets – email notification platform
Deploy an Azure Application Gateway
The aim of this blog is to easily deploy an Azure Application Gateway Standard_v2 tier via Powershell. Identify a dedicated application gateway subnet which will host only application gateways. No other resources will be allowed in this subnet. Deployment Plan: Deployment Steps: Step 1 – Create a resource group container for the application gateway resources.… Continue reading Deploy an Azure Application Gateway
Configure certificate auto-rotation
An Azure Key Vault provides the capability for you to easily provision, manage, and deploy your digital certificates. In this blog, you can update your certificate’s validity period, auto-rotation frequency, email notification contacts and CA attributes. The certificates can be public or private SSL / TLS certificates which may be: A self-signed certificate,A certificate created… Continue reading Configure certificate auto-rotation
Configure key rotation
Automated cryptographic key rotation allows users to configure the Key Vault to automatically generate a new key version at a specified frequency, using a key rotation policy manually defined on each individual key. It is recommended to rotate encryption keys at least every two years as per best practices. Automated cryptographic key rotation can also be… Continue reading Configure key rotation
Azure OpenAI Private Endpoints
The aim of this blog is to simplify the security hardening of your Azure OpenAI infrastructure using private endpoints instead of allowing the OpenAI traffic to traverse the public internet. A private endpoint is a network interface that uses a private IP address allocated from your target virtual network. This network interface connects you privately… Continue reading Azure OpenAI Private Endpoints
Fortinet FortiManager (HA) Template deployment
The aim of this blog is to simplify the deployment of the Fortinet FortiManager HA on Azure. This solution enhances the availability of the FortiManager platform by deploying instances across multiple Availability Zones. The FortiManager HA failover process still requires manual intervention and is not automated. FortiManager provides automation-driven centralized management of your Fortinet devices… Continue reading Fortinet FortiManager (HA) Template deployment
Fortinet FortiAnalyzer (HA) Template deployment
The aim of this blog is to simplify the deployment of the Fortinet FortiAnalyzer HA on Azure. This solution enhances the availability of the FortiAnalyzer platform by deploying instances across multiple Availability Zones. FortiAnalyzer provides centralized collection, storage and analysis logging from all Fortinet security devices including FortiGate Next-Generation Firewalls, VPNs, and intrusion detection and… Continue reading Fortinet FortiAnalyzer (HA) Template deployment
Fortinet FortiManager single instance Template deployment
This blog aims to easily deploy a single instance Fortinet FortiManager instance using an ARM template to allow for re-deployment if required. In my next blog, I will unpack how the Fortinet FortiManager can also be deployed as a FortiManager HA cluster and can have up to a maximum of five units: one primary unit… Continue reading Fortinet FortiManager single instance Template deployment
Trend Micro Cloud One (HA) Fallback
The aim of this blog is to simplify the enablement of the High Availbility Function App on an existing Trend Micro Cloud One Scale Set. Instructions on how to provision a Trend Micro Cloud One scale set in Azure can be found here. Deployment Plan Step 1 – Identify your Firewall subnetStep 2 – Identify… Continue reading Trend Micro Cloud One (HA) Fallback